With new and evolving cybersecurity threats emerging almost daily, the risk to businesses is greater than ever. A 2023 study by IBM reports that the average cost of a data breach in Australia is now $4.3 million. While this figure is less than the global average of $4.45 million, the escalation of cybersecurity threats shows no sign of slowing anytime soon.
So, the critical question is, how do you keep your organisation safe in such a hostile cyber environment? The best place to start is by educating yourself on the nature of cybersecurity risks and the options available to help mitigate them.
In this post, we discuss the top five cybersecurity threats to be aware of in 2024. These are the most common threats that we see in our work helping clients mitigate these risks and respond to incidents.
1. Increased Impact from Malicious AI Tools
Artificial Intelligence (AI) poses a significant threat, not just as a tool for innovation but also as a potential weapon in the hands of cybercriminals.
AI can be exploited by cybercriminals to conduct more sophisticated attacks with increased precision and frequency. These AI-driven attacks can bypass traditional cybersecurity measures, making detection and defence more challenging for organisations.
Strategies to Combat Malicious AI Tools:
Developing strategies to counteract malevolent AI tools is important for safeguarding your organisation against complex threats. By remaining proactive and employing security practices, you can diminish the risks and consequences of AI-powered cyber-attacks. Here are helpful strategies to combat these threats:
- Continuous Monitoring: Implement AI-driven security tools that monitor network activity to detect and respond to anomalies. These tools can detect anomalies and respond promptly to any suspicious behaviour.
- Advanced Threat Intelligence: Leverage platforms that use AI to predict and identify potential threats before they can cause harm.
- Regular Security Audits: Conduct frequent cybersecurity risk assessments to identify vulnerabilities and ensure all security protocols are up to date.
Organisations can enhance their protection against the increasing threat of malicious AI by staying proactive and utilising AI defence tools.
2. Phishing
Phishing is one of the most common forms of attack whereby fake emails are sent purporting to be from sources familiar to the target, such as the Commonwealth Bank, Australia Post or Microsoft. The goal of phishing is to trick individuals into granting access to secure systems by either handing over password details or allowing the installation of malware onto their computer. Once the attacker has gained access to company systems, they may explore and plan their next steps undetected.
Protecting Against Phishing
- Multi-factor Authentication (MFA): Even if an attacker obtains password details, MFA adds a layer of security. Most modern applications support MFA, though it may not be enabled by default.
- Email Filtering: Effective email filtering can stop many phishing emails before they reach employee inboxes. Advanced filtering is available for major platforms like Microsoft Office 365.
- User Education: Employee awareness is critical. Educating your workforce on recognising and avoiding phishing attacks is an effective risk mitigation strategy.
3. Business Email Compromise
Business email compromise is a strategy used by attackers to defraud a target company, employed once they have gained access to secure systems via other means. With access to company systems, they will gather information regarding financial processes, payment systems and client relationships. They will monitor email communications to learn who in the organisation has financial authority and the language and methods that they use to communicate.
Once they have the information that they need, attackers will then seek to deceive employees, clients and business partners into making payments to their bank accounts rather than genuine ones. These fraudulent requests for funds can be difficult to identify and lost funds can be challenging to trace and recover. The potential for direct financial loss through business email compromise is significant.
Protecting Against Business Email Compromise
- Multi-factor Authentication (MFA): MFA effectively defends against many user account attacks.
- User Education: Employees involved in financial transactions must be vigilant and take all necessary precautions.
- Verification Processes: Implement secondary verification (e.g., phone calls) for all financial transactions and change of detail requests.
4. Social Engineering
Cybercriminals will often seek to gain the trust of their targets in order to elicit the information that they need to breach secure systems. Any form of social interaction with the malicious intent of gaining access to secure systems can be considered social engineering. A common approach is to create fictitious personas on social media which are then used to establish fake relationships with potential victims and trick them into allowing access to company systems.
Protecting Against Social Engineering
- User Education: Training employees to identify and respond to social engineering threats is essential.
- Endpoint Protection: Use advanced endpoint protection software to detect and block malicious software.
- Multi-factor Authentication (MFA): MFA provides robust defence against user account breaches, even if passwords are compromised.
5. Ransomware
Ransomware is a particular form of malicious software (aka malware) that, once active within a computer system, will encrypt critical data rendering it inaccessible until a ransom is paid. Unfortunately for some business owners, even when a ransom is paid, access to the data is not always restored. Ransomware is responsible for some of the largest and highest profile security incidents in recent times. A ransomware attack can be devastating to any organisation, grinding operations to a halt.
Protecting against Ransomware
All forms of malware including ransomware can be mitigated with strategies such as:
- Endpoint protection: All computer systems must be protected with advanced endpoint protection software.
- System updates: Computer systems without up-to-date software and operating systems are a common weakness that attackers can exploit.
- Isolated backups: Not only should backups be monitoring and tested regularly, but a copy should be stored separately and unattached to the main systems to protect attackers from being able to compromise backups.
- User education: Human error is common factor in many malware infections. Training employees to recognise a potential malware infection and respond accordingly is critical.
6. Supply Chain Attack
A supply chain attack is a form of cyber-attack where malicious actors target an organisation indirectly through less secure partners in their supply chain, most commonly software vendors. The attackers aim to compromise a particular software application which, once deployed in the target organisation’s network, allows unauthorised access to company systems. Such attacks can have widespread repercussions, as compromising one link in the supply chain can potentially grant access to multiple interconnected organisations.
Although not strictly a supply chain attack, it’s important to highlight the necessity for supply chain cyber-resilience. An attack on your supply chain can be just as disruptive as an attack through your supply chain. Disruptions to key suppliers can cause significant operational downtime and extend vulnerabilities within your organisation.
Protecting against Supply Chain Attack
- Risk management: Include Supply Chain in risk management plans, including disaster recovery and cybersecurity incidents.
- Least trust security: Limit supplier access to the minimum required.
- Vendor security requirements: Incorporate clear vendor security requirements into supply agreements.
Watch our free on-demand webinar now: Managing the Risk of Supply Chain Attack.
Conclusion
Cybersecurity starts with an understanding of the threats that your organisation may face, and the options available to you to mitigate those risks. From there you can prioritise and focus your cybersecurity efforts with confidence.
For help protecting your business, speak with one of our cybersecurity experts today.
In today’s digital era, cybersecurity threats are an ever-present and evolving danger. Organisations, regardless of size, are at constant risk of cyberattacks, including ransomware and data breaches. The increasing sophistication of these threats demands an advanced level of vigilance and response, which brings Managed Detection and Response (MDR) into the spotlight.
What is Managed Detection and Response (MDR)?
MDR is a comprehensive cybersecurity service that offers round-the-clock monitoring and response to cyber threats. It’s not just another line of defence; it’s a strategic approach that combines technology, processes, and importantly, human expertise to identify and mitigate cyber risks effectively. Although an oversimplification, it may be helpful to consider MDR as being a combination of SIEM (security monitoring & alerting) + security software (such as endpoint protection agents) + SOC (A team of security experts on standby to respond).
To better understand this, it can help to consider where MDR fits in relation to other alternative approaches to cybersecurity. To illustrate this we will compare MDR to three other common offerings: Unmanaged cybersecurity, Cybersecurity managed by an MSP/TSP and finally a specialist Managed Security Services Provider (MSSP) engagement.
Unmanaged Cybersecurity
Unmanaged cybersecurity generally involves having one or more basic cybersecurity products deployed, such as endpoint protection agents, but without any oversight or management of those products, or any broader cybersecurity strategy. Cybersecurity products are likely configured with default settings and may or may not be functioning effectively. In the event of a cybersecurity incident, the organisation will likely remain oblivious until it’s far too late and significant damage is done.
By comparison MDR will be more expensive but will also be far more effective in protecting the organisation. MDR will not provide a holistic cybersecurity strategy or oversight for the entire organisation, so security gaps are likely to remain, but for the areas where MDR is deployed, security will be tight, and responses to any potential incidents will be rapid.
MSP Managed Cybersecurity
Of the scenarios presented here, the most common is where the organisation engages a Managed Services Provider (MSP) to provide not only cybersecurity services, but other IT services such as end-user helpdesk and cloud services. Commonly the MSP will help with cybersecurity strategy and the deployment of various cybersecurity products and controls, as well as the ongoing management of these solutions.
The existence of a broader cybersecurity strategy and oversight means that gaps in protection are less likely, compared to unmanaged cybersecurity, but still not entirely ruled out. The MSP will respond to any cybersecurity incidents detected, however is unlikely to respond as rapidly as an MDR solution would, nor with the same deep level of technical expertise that and MDR brings. The ideal scenario is to engage both an MSP and an MDR solution.
MSSP Managed Cybersecurity
A Managed Security Services Providers (MSSPs) operates on a similar model to an MSP but with a narrow focus on cybersecurity. They will bring a deep level of technical expertise, with a team of dedicated security analysts and engineers. The MSSP’s response to any detected incident will likely be faster and more technically capable than that of an MSP due to the specialised nature of its services.
Engaging with a specialist MSSP can provide a level of security and response that surpasses both MSP and MDR solutions, but this comes at a higher cost. Additionally, MSSPs may not have the same level of understanding or familiarity with an organisation’s unique IT environment compared to an MSP who has been managing their IT services for some time. For organisations requiring this level of cybersecurity response, engaging both an MSP and an MSSP to work closely together will provide the best outcome.
The Advantages of Managed Detection Response (MDR)
Managed Detection & Response offers several unique advantages that set it apart from other common cybersecurity solutions.
- Continuous Monitoring and Rapid Response: Cyber threats don’t adhere to a 9-to-5 schedule. MDR provides 24/7 monitoring, ensuring that threats are identified and addressed promptly, often within minutes. Many other cybersecurity offerings may monitor 24×7, however responding to incidents may take signification longer.
- Expertise and Specialisation: MDR services are not simply automated technology but are manned by cybersecurity experts who specialise in threat detection and response, bringing a level of expertise that other purely automated solutions can’t match.
- Advanced Technologies and AI Integration: MDR services leverage advanced technologies, including Artificial Intelligence (AI) and Machine Learning (ML), to enhance threat detection capabilities.
- Customisation and Scalability: MDR solutions can be tailored to fit the specific needs of an organisation, scaling as the organisation grows or as threats evolve. Many other comparable cybersecurity solutions are either too large and expensive for many organisations or alternatively may fail to scale effectively beyond a certain size.
- Cost-Effectiveness: Building and maintaining a comparable in-house security operation can be prohibitively expensive, whether this in-house team is your own, or run by your main technology partner or MSP. MDR services offer a cost-effective alternative, providing top-tier security expertise without the overhead of in-house or boutique engagements.
The Role of Managed Detection Response (MDR) in Modern Business
MDR services play an extremely important role in modern business, addressing business and security requirements that many other cybersecurity solutions cannot.
Protecting Against Ransomware and Data Breaches
Ransomware attacks and data breaches can have devastating effects on businesses. MDR plays a critical role in not only preventing these attacks but also in minimising the impact if they occur, with 24×7 human lead incident response.
Addressing the Cybersecurity Talent Shortage
The cybersecurity industry faces a significant talent shortage. MDR services help bridge this gap by providing access to an extensive team of experts, thus alleviating the pressure on in-house resources, or avoiding the rapidly increasing costs of boutique cybersecurity providers.
Compliance and Regulatory Requirements
Many industries face stringent regulatory requirements regarding data protection and cybersecurity, not to mention increasing challenges in qualifying for cyber insurance coverage. MDR services help ensure compliance with regulations, avoiding potential legal and financial penalties, while helping to satisfy insurers’ stringent requirements.
Managed Detection Response (MDR): The Human Touch
While technology is a critical component of MDR, the human element is what sets MDR services apart from other purely product-based cybersecurity solutions. Skilled cybersecurity professionals bring a level of intuition and experience that cannot be replicated by machines alone.
MDR teams comprise individuals with diverse backgrounds in cybersecurity, offering a blend of skills that range from threat hunting to incident response. This human oversight ensures that the subtleties of cyber threats are not overlooked.
Effective MDR services foster collaboration between the service provider and the client. Regular communication and reporting ensure that clients are aware of their security posture and any actions taken on their behalf.
The Future of Managed Detection Response (MDR)
Looking ahead, the role of MDR in cybersecurity is only set to grow. As cyber threats become more sophisticated, the need for comprehensive, responsive, and expert-driven cybersecurity solutions will become more pronounced.
As new technologies emerge, MDR services will evolve to incorporate these advancements, further enhancing their threat detection and response capabilities.
Conclusion
Managed Detection and Response represents a significant advancement in the field of cybersecurity. It offers a dynamic, expert-driven solution to the complex and ever-changing landscape of cyber threats. For businesses looking to bolster their cybersecurity posture, MDR presents a comprehensive, effective, and adaptable solution, ensuring peace of mind in an increasingly digital world.
Technology and the internet play a crucial role in the day-to-day operations of non-profit organisations of all sizes, from small volunteer-run operations to huge worldwide groups like the Red Cross. From fundraising to communication with donors and volunteers, technology has made these tasks more efficient and effective. However, this increased use of technology also brings about heightened risks of cybersecurity threats.
According to statistics from the 2020 Global Risk Report by the World Economic Forum, cyberattacks are among the top 5 global risks in terms of likelihood. This means that organisations, including non-profits, need to take cybersecurity seriously in order to protect their assets and data.
The unique cybersecurity challenges for non-profits
Not only are non-profit organisations often handling sensitive data, such as donor and beneficiary details, but they may also be responsible for substantial funds, making them an attractive target for cyber criminals. Add to this that many non-profits operate with smaller teams and budgets, and it becomes clear that many may face unique challenges when it comes to cybersecurity.
Unfortunately, many non-profit organisations are ill-prepared to handle cyber threats, leaving them vulnerable to attacks with potentially devastating consequences, such as:
Financial Loss
A successful cyberattack on a non-profit can result in direct financial losses from stolen funds or ransomware, not to mention costs involved in recovering from the incident and returning operations to normal. This can be particularly damaging for smaller non-profits with limited resources, or those without cyber-insurance coverage.
Reputational Damage
The loss of sensitive data, especially if it involves personal or financial information of donors and beneficiaries, can severely damage the trust and confidence placed in the organisation. This could result in a loss of supporters and volunteers, making it harder for non-profits to achieve their goals.
Legal & Compliance Consequences
Non-profits are also held to the same legal and compliance standards as for-profit organisations when it comes to protecting sensitive data. Failure to comply with these regulations could result in legal consequences, fines, and reputational damage.
Low-cost cybersecurity strategies for non-profit organisations
Given the competing priorities of increasing risks of cyber threats and staying focussed on mission, it is important for non-profit organisations to make the most of effective, right sized and cost-efficient cybersecurity strategies. Here are some key strategies that we have had success with when working with non-profit clients to improve their cybersecurity.
Employee training & awareness
One of the most vulnerable areas of any organisation’s cybersecurity is its employees. It is crucial for non-profits to provide cybersecurity awareness training to all staff members, including volunteers, on safe internet practices and how to identify potential threats.
As well as commercially available cybersecurity awareness training offerings, there are plenty of free resources available online, such as on YouTube. Running internal training sessions and information sharing workshops is also free and easy, and an excellent way of building cybersecurity awareness amongst staff and volunteers.
Read more: Building a culture of cybersecurity awareness
Vendor donations & discounted software
Non-profits can take advantage of vendor donation programs to obtain a range of technology solutions including cybersecurity software and tools either at a reduced price or for free. Many technology companies such as Microsoft, Canva and Xero have programs specifically designed for non-profits that offer discounted or donated products and services.
As an example of what’s available, Microsoft offers up to 10 free licenses of Microsoft 365 Business Premium to qualifying non-profit organisations in Australia, with deep discounts for additional licensing over the initial 10. How can this help non-profit cybersecurity? Microsoft 365 Business Premium includes many advanced cybersecurity features that other plans do not. Without these discounts many non-profits would be forced to rely on cheaper alternatives, missing out on important security & data protection benefits.
Partners that understand non-profits
When selecting a non-profit technology partner, decision makers should consider companies that understand the unique challenges and needs of non-profit organisations. IT partners who are well-versed in the non-profit sector are not just vendors; they are collaborators who align closely with the mission and values of the non-profit.
This alignment is crucial, as it translates into more than just technical support – it’s about providing cost-effective and mission-driven solutions. The right IT partner is not just a service provider but a strategic ally – one that empowers the non-profit to focus on their core mission, knowing that their technology needs are in capable and understanding hands. This is important to ensure that non-profit cybersecurity solutions are carefully considered and right sized for the unique needs of the organisation, taking into consideration the organisational strategy, key risk areas and various constraints.
Don’t neglect the fundamentals
While it may seem that advanced technology is the key to cybersecurity, organisations should not neglect the fundamentals. Simple measures like regular data backups and regular updates of software and operating systems can go a long way in preventing cyberattacks.
Additionally, having strong password policies and enforcing multi-factor authentication will also add an extremely effective layer of security. These measures are often low-cost or even free, making them easily accessible for non-profits with limited budgets.
The importance of robust cybersecurity measures for non-profits
While non-profit organisations may face unique challenges in the realm of cybersecurity, there are also a variety of strategies and resources available to help them improve their defenses. Grassroots IT has deep expertise working with non-profit organisations and understands the importance of providing cost-effective solutions that align with their missions and values. To speak with a non-profit technology expert, contact us today.
Defining your IT strategy is a powerful step towards success, yet alarmingly we still find organisations that don’t take the time to clarify what they expect or require from IT. At its simplest your IT strategy is a statement of how you intend to use IT to support your over-arching business goals. You don’t have unlimited resources to spend on IT, so your IT strategy is there to clarify where you will focus your efforts, and equally as important where you will not.
In our work with clients formulating and executing on their IT strategies we often see clear trends emerging over time in response to the ever-changing IT landscape. Of course, every company will have their own unique IT strategy, but common patterns can emerge.
As we work with our clients in preparation for the year ahead, we are seeing the following three themes appearing with consistency.
Related: Why aligning your IT strategy with business goals is critical for success
User Experience
In response to the pandemic the world of work has changed significantly, also significantly shifting how people relate to their employment, the environments they work in, and the tools that they are expected to use. Simply put, user experience has become a critical element in every IT strategy.
But what does this mean for your organisation? It means that employees are expecting easy-to-use, efficient and user-friendly technology solutions that allow them to do their job effectively from any location. This includes everything from remote working tools to cloud-based collaboration platforms, all accessible as easily from their smartphone as their home office.
They are also expecting to have fingertip access to the information and expertise that they need, with top-tier training and support services available when required.
So, as you plan your IT strategy for 2024, make sure that user experience is at the forefront of your decision making and investment plans. Put yourself in the shoes of your employees and consider their daily tasks and interactions with technology – are they seamless, intuitive and empowering? If not, it’s time to make some changes.
Cybersecurity
As technology continues to evolve and become increasingly intertwined with our daily lives, the risk of cyber-attacks and data breaches has also risen exponentially. Cybersecurity is no longer just a concern for IT departments but should be a top priority for every organisation’s IT strategy, with direct board-level oversight.
A strong cybersecurity plan should include regular security audits, employee training on identifying and handling potential threats, as well as implementing the latest security software and protocols. Importantly in the post-pandemic world, your cybersecurity plan must also consider new ways of working. With many staff now working from home, old ways of securing your organisation may no longer be as effective.
Cybersecurity not a one-and-done task, but an ongoing process that must be continuously monitored and updated to stay ahead of potential threats. Make sure that your IT strategy reflects this and allocate appropriate resources to keep your organisation’s data safe and secure.
AI & Automation
2023 was the year that artificial intelligence hit the mainstream, with the release of ChatGPT throwing the floodgates open. The new-found accessibility of AI is emerging as an inflection point on the longer-term trend of business process automation, with the combination of the two promising significant opportunities.
AI and automation can streamline processes, improve efficiency, and reduce costs in almost every area of your organisation – from customer service to HR to supply chain management. It can also provide valuable insights and data analysis that humans may miss. As the technology continues to advance, it will only become more powerful and integrated with our daily lives.
It’s no longer a question of if but when AI and automation will become an integral part of every IT strategy. So, in the year ahead, make sure that you’re keeping up with the latest developments and considering how it can enhance your organisation’s operations and drive growth.
Conclusion
As we move towards 2024, it’s clear that user experience, cybersecurity and AI/Automation will continue to be pivotal elements of every IT strategy. Organisations must prioritize these areas to stay competitive and meet the evolving needs of their employees and customers. With a strong focus on these essential components, your IT strategy can serve as a roadmap for success in the ever-changing digital landscape.
Keep in mind, however, that these are just three of many elements to consider when crafting your IT strategy. As technology continues to advance, new challenges and opportunities will arise, requiring organisations to stay agile and adaptable.
Grassroots IT has many years of experience working with clients to formulate IT strategies that align with business goals and lead to tangible results. If you would like to talk about your IT strategy, contact us today.
As businesses increasingly migrate to digital platforms, cybersecurity has become a non-negotiable priority. Microsoft 365 leads the way in providing robust security solutions and offers an abundance of features designed to safeguard your business data and systems – but how do you navigate the plethora of options available to ensure that you’re choosing the best security measures for your specific needs without feeling overwhelmed? Enter Microsoft Secure Score.
Just as the name suggests, Microsoft Secure Score is a built-in tool that not only scores your security posture but also recommends actions for improvement. With Secure Score, enhancing your cybersecurity is no longer a daunting task but a series of quick, actionable wins that will strengthen your defence line further against potential threats.
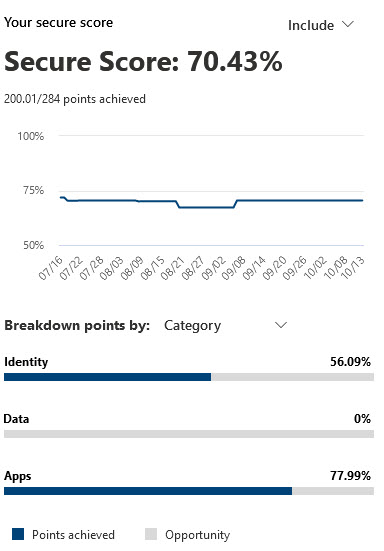
What is Microsoft Secure Score?
Secure Score is a free tool that comes with Microsoft 365 that analyses your organization’s security stance based on your unique use of Microsoft 365 services. It provides a numerical score, along with a detailed breakdown, of how well you are implementing the recommended security controls. Quite simply, the higher your Secure Score, the lower your risk level.
Secure Score monitors Identity, Apps, Data, and Devices in Microsoft 365, helping you to report on the current state of your security posture, suggest improvements by providing guidance, visibility and control, and compare yourself against similar sized organisations.
Importantly, it does not simply focus on one specific area of security in your Office 365 environment. Instead, it looks at all products available under your current licensing and providing recommended actions across multiple areas. Recommendations are presented in an easy-to-understand dashboard, grouped by product, and sorted by the impact the recommended change will have on improving the security of your Microsoft 365 environment. This approach makes it easy to focus your efforts in the right area and avoid spending unnecessary time on actions that won’t move the needle as much.
Key features of Secure Score
Key features of include:
Security Recommendations
Secure Score provides actionable security recommendations tailored to an organization’s specific environment. These recommendations cover areas like identity and access management, data protection, threat detection, and more.
Point-Based Scoring
Each recommended security improvement comes with a point value. By implementing the recommendations, your organization can earn points and increase your Score.
Comparison and Benchmarking
Secure Score allows you to compare your security posture with industry benchmarks and similar organizations. This feature provides valuable insights into how well you are performing relative to your peers.
Threat Intelligence Integration
The tool integrates with Microsoft Threat Protection, offering real-time threat intelligence and helping you stay ahead of emerging threats.
Historical Tracking
The system maintains a historical record of progress, enabling you to visualize your security journey and measure improvements over time.
Why use Microsoft Secure Score?
Microsoft Secure Score provides high impact recommendations to improve your cybersecurity posture, usually requiring little or no additional expense. Rather than requiring new and additional security services, Secure Score simply helps you to make the most of the features that you already have access to within the Microsoft 365 platform.
Importantly, Secure Score may help you reduce your cyber-insurance premiums. With cyber-insurance becoming a vital piece of any cybersecurity strategy, many insurers are now recognising the value of Microsoft Secure Score and factoring it in when calculating insurance premiums. Improve your Secure Score and you can potentially reduce your cyber-insurance premiums.
Not only that, but if your organisation aligns with one of the recognised cybersecurity frameworks, such as the Essential Eight, improving your Secure Score can also positively impact your alignment with your chosen framework.
Using Microsoft Secure Score
You can find your Secure Score in the Microsoft Defender Portal. Navigating the portal is quite intuitive, allowing you to focus on the insights and recommendations provided. Importantly, each recommended action also provides details on how the action will impact your security standing, along with any potential user impact.
Recommendations may range from reviewing an existing policy to implementing changes that may have a significant impact on users completing everyday tasks. As with all such changes, it’s important that you carefully assess the recommendation and consider the potential impact on operations.
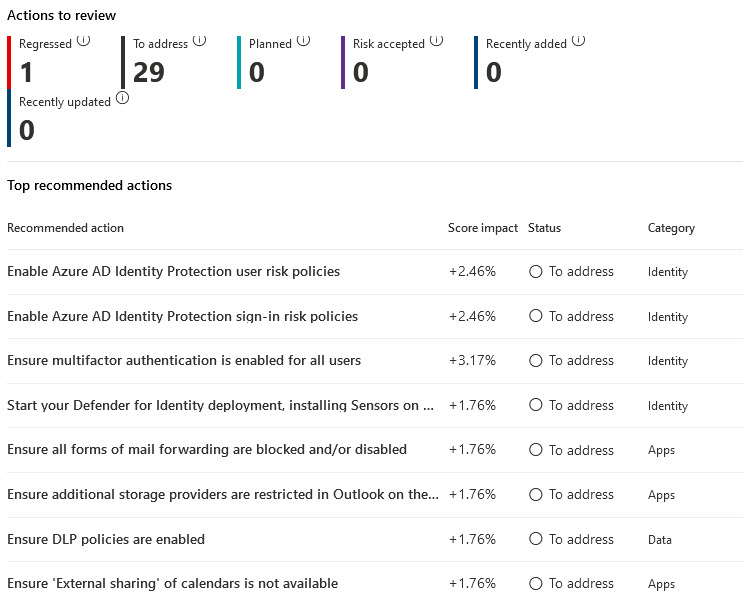
Reporting and Tracking with Secure Score
When embarking on a process of change, it’s important to measure and demonstrate progress over time. Thankfully the Secure Score portal provides a historical view of your organisations score over the last 90 days, showing a trend line that makes sudden changes easily visible. A list of recommended actions is also shown, showing when there was a change to each action, if points were gained or lost and allowing you to understand sudden changes in score.
The Secure Score dashboard shows different metrics and trends, where an action may have regressed, recent decreases, points achieved, along with a comparison against similar sized organisations. Metrics and trends can be shown over 7, 30, & 90 days or using a custom date range and can be filtered based on the 4 main categories Secure Score applies against.
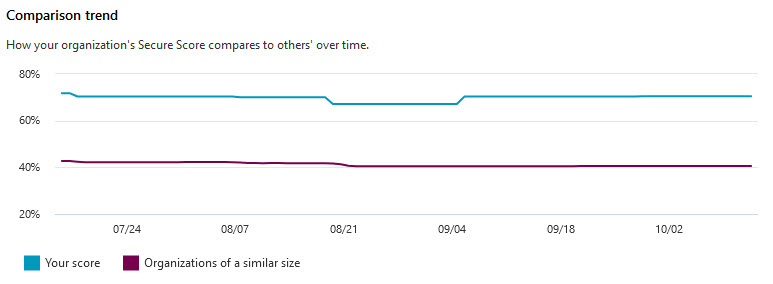
Safely Implementing Changes (without the drama)
Unfortunately, there are too many stories of (easily avoided) problems being created when security changes are made without proper consideration. One story that we’ve heard too many times is when an over-enthusiastic sysadmin has enabled multi-factor authentication or conditional access policies within Microsoft 365 without properly preparing the organisation – thus effectively locking many, if not all, staff out of the system. Problems like this are easily avoided though, with appropriate forethought and planning.
For many clients we find that an effective approach is to develop a roadmap of changes based on the Secure Score recommendations, and then progressively work through these changes over a period of weeks, reviewing improvements in their Secure Score as they go. Some changes may be quick and easy to implement, while others may require more careful management, such as technical change control and user training. By approaching this as a progressive roadmap of smaller actions you can ensure ongoing improvement while managing the risk of disruption.
How we improved both user experience and security with secure score
Grassroots IT recently helped a mid-sized non-profit organisation that was struggling with their systems. They reported inconsistent user experience across their Tenant, no defined settings for users when accessing systems and their users didn’t trust that they could easily access Office 365. When a review was conducted of the organisation’s Secure Score, it was immediately apparent that there were problems with both Identity and Apps within their tenant.
Utilising the recommended actions in Secure Score, Grassroots IT was able to implement multiple changes to their environment that made the user experience easier while also improving their overall security posture. Some of these changes included simplifying the user login process, enabling self-serve password recovery and using a single authentication service for apps. At the same time, multifactor authentication was enabled for all users, and appropriate policies were implemented to protect users from malicious content and emails, significantly improving their Secure Score and security posture.
Additional Resources
Microsoft Secure Score is a powerful tool for improving the security of your Microsoft 365 environment. To learn more, speak to us today, or explore some of these additional resources.
In a post-pandemic world, flexible working arrangements have become the norm for many. Where working remotely was previously the exclusive domain of salespeople and on-site consultants, these days an office full of staff seems a rare sight, with online meetings commonplace.
While the long-term future of work is still unclear, it’s fair to say that remote working in some form is here to stay, bringing with it new challenges for business leaders, not least of all those tasked with cybersecurity. Old approaches to securing the organisations digital assets have been rendered outdated, while new unforeseen risks have emerged almost overnight.
So, what are the most pressing cybersecurity risks with a remote workforce, and how do you ensure the ongoing protection of your business in light of these changing threats?
Understanding the risks
The various tools and techniques that cyber criminals employ to attack those working from home are generally no different to those used elsewhere, however in a work-from-home context some threats are greater than others and can pose unique challenges. Here are three of the highest risk cyber-threats for staff working from home.
Phishing & other scams
Phishing and other such scams are fraudulent attempts to obtain sensitive information from users, such as usernames, passwords and credit card details, usually by sending fake email purporting to be from a known, trusted person or brand. WFH users are often more vulnerable to such attacks as they may not have the same level of active awareness as others, may use personal email accounts alongside work email, and may not have ready access to corporate security tools and support.
Read more: How to identify a phishing email
Device security
Device security refers to the protection of physical computing devices, such as laptops, smartphones and tablets against unauthorised access which would in turn give cybercriminals access to confidential corporate information. This is of particular concern with staff working from home as physical security of devices is likely to be less than in an office environment, particularly when others have access to the same work environment at home.
Home workers are also more likely to use personal computing devices rather than business supplied devices, with or without explicit permission to do so. Personal devices are likely not configured with the same security controls as company-owned devices, nor actively monitored, managed or updated with the latest security updates.
Data leakage
Data leakage is the unauthorised transmission of data from within the company to an external destination or recipient, whether intentionally or otherwise. Users working from home are likely to use a poorly secured home network, have inadequate access controls in place around confidential information, and may even use personal cloud services instead of, or alongside approved company services, all of which pose the very real risk of leaking important company information.
Implementing Solutions
The good news is that there are proven strategies for effectively mitigating each of these threats in a work-from-home scenario.
Cloud Platforms
Cloud platforms such as Microsoft 365 are by nature designed to support remote working. It doesn’t matter whether you are physically in the office, at home or on a client site, the way you access a cloud service, and the security controls available are the same. By their very nature this makes cloud platforms a better, and potentially more secure option for supporting home-based workers than traditional infrastructure solutions.
Device Management
Ensuring the security of physical devices at home presents a unique challenge best addressed by strong policy. A work-from-home policy must enforce the use of company-owned devices only, enabling the deployment of strong security controls to the device such as patch management, managed detection & response agents and data encryption. The policy must also discuss the physical security of devices, the use of automatic screen locking and immediate mandatory reporting if a device is misplaced.
It is worth briefly mentioning the topic of Bring-you-own-device (BYOD), whereby staff may use their own devices to access corporate systems. Allowing for BYOD is a perfectly valid option, however, please be aware of the security implications of such a policy and adjust accordingly.
Employee training
A strong culture of cybersecurity awareness can be one of your most effective defences against security breach and data loss, and especially so when staff work from home. Users must be well versed on recognising threats such as phishing emails and how they should respond. They should also be clear on all relevant policies and understand the importance of compliance.
Read more: Building a culture of cybersecurity awareness in your business.
Conclusion
The post-pandemic work-from-home movement is here to stay, with undeniable benefits for many people. It does however bring with it unique cybersecurity risks that the organisation must proactively address to avoid inadvertently allowing cyber criminals access to corporate systems.
Grassroots IT is well versed in helping our clients support their home-based workers with secure, scalable systems. For help protecting your remote workers contact us today.
Explore Common Cybersecurity Myths and Misconceptions
In the digital age, cybersecurity has become a critical concern for businesses of all sizes. However, there are numerous misconceptions surrounding this complex field that can lead to complacency and, ultimately, vulnerability. In this post, we debunk ten of the most common cybersecurity myths that could be putting your business at risk.
Myth 1: My business is too small/boring to be attractive to hackers
Every business, regardless of its size or industry, is a potential target for cybercriminals. Small businesses often fall into the trap of believing they’re too insignificant to attract attention. However, hackers often target smaller businesses precisely because they tend to have weaker security measures in place. With many cyber-attacks launched at scale (eg: phishing emails) the incremental cost to hackers of targeting your small, boring business is negligible, yet the potential pay-off can still be significant.
Myth 2: My data is safe in the cloud
While cloud storage providers implement robust security measures, it doesn’t mean your data is invincible. Cybercriminals have been known to breach cloud security, and human errors can also lead to data exposure. It’s crucial to understand the shared responsibility model of cloud security and ensure you’re doing your part to protect your data. The cloud providers provide the platform, and the means to secure your data, but ultimately the responsibility for doing so is yours.
Read more: 5 Critical Questions to Ask About Your Microsoft 365 Security
Myth 3: My data is safe on my own server
Storing data on your own server doesn’t automatically make it safe. Without proper security measures in place, your server can be just as vulnerable as any cloud service. Regular updates, patches, and strong access controls are essential to protect your data (many of which are automatically done for you in the cloud).
Myth 4: Cybersecurity is my MSPs responsibility
While your IT department or MSP plays a crucial role in implementing and maintaining security measures, cybersecurity is everyone’s responsibility from the bottom of the org chart all the way to the board. A commitment to cybersecurity must be lead from the top, with company directors and CEOs holding particular responsibilities for protecting the organization’s digital assets.
Read more: 5 questions board members need to ask about cybersecurity
Myth 5: My team works from home, so security is their responsibility
Remote work has blurred the lines of responsibility for cybersecurity. However, as an employer, it’s your duty to provide secure systems and training to your employees. This includes secure communication tools like Microsoft Teams, and guidelines on safe online practices.
Myth 6: Cybersecurity is too expensive
With the average cost of a data breach in Australia reaching $4.4 million, the cost of a data breach can far outweigh the investment in cybersecurity. While implementing robust security measures may require an upfront investment, this can be far less costly than the potential financial and reputational damage caused by a breach.
Myth 7: I’ll know if my systems have been hacked
Many breaches go undetected for months, or even years. Cybercriminals often aim to infiltrate systems without detection, stealing data or causing damage over time. Regular system audits and monitoring are essential to detect and respond to breaches promptly.
Learn more: 24×7 peace of mind with managed detection & response
Myth 8: My staff are too smart to get hacked
Even the smartest individuals can fall victim to sophisticated cyberattacks. Phishing attacks, in particular, have become increasingly convincing and can easily trick unsuspecting users. Regular training and cybersecurity awareness are crucial to equip your staff with the knowledge to identify and avoid such threats.
Read more: Building a culture of cybersecurity awareness in your business
Myth 9: Strong passwords are enough
While strong passwords are a fundamental part of cybersecurity, they’re not a panacea. Multi-factor authentication (MFA), secure network connections, and regular software updates are just as important in protecting your systems.
Myth 10: We only need to protect against external hackers
Insider threats, whether malicious or accidental, are a significant risk. Employees can inadvertently cause a breach by clicking on a malicious link or misconfiguring a database. Regular training, strict access controls, and monitoring can help mitigate this risk.
Dispel Cybersecurity Myths To Protect Your Business!
Cybersecurity is a complex field that requires a proactive and informed approach. In the realm of cybersecurity, complacency can be your biggest enemy. Grassroots IT are cybersecurity experts, ready to help secure your business against cyber criminals. To see how we can help, speak with us today.
Microsoft Office 365 is built from the ground up to be a highly secure platform, but that doesn’t necessarily mean that your own Office 365 environment is configured securely. There are numerous different ways that organisations can use Office 365, and just as many ways that it can be configured.
Ultimately the responsibility for securing your Office 365 environment, and the information and data stored in there, rests with you. Microsoft provides the platform and the means, but it’s up to you to consider your unique situation and ensure that appropriate security measures are taken.
So how do you know if your Office 365 environment is secure? Every organisation is different, and with so many ways of using and securing Office 365 there is no one-size-fits-all solution. The good news is that there are some well-established best-practices that can significantly strengthen the security of your environment.
Here are five critical questions that you need to ask about your Office 365 security to ensure that you’re properly protected.
#1. What Microsoft Office 365 plan do we use?
Let me start by saying that Microsoft has a frustrating habit of changing product names and bundles regularly, which can lead to some confusion. So, for the sake of clarity, let me share a bit of history with you.
First there were the Office 365 plans, offering a suite of products such as Word, Excel, Email and Teams. Then Microsoft added a whole new line of plans called Microsoft 365, which included all the things from Office 365, plus added a whole lot more, mainly to do with security and governance. Then more recently the Office 365 name has been retired entirely, leaving only Microsoft 365 plans to choose from. If you were using Office 365 plans before these changes happened, you will still be on those same Office 365 plans now.
It’s important to understand which Microsoft Office 365 plan you subscribe to, because not all of them have access to the better security features. For most organisations, we recommend that you subscribe to the Microsoft 365 Business Premium plan, or for some larger organisations, the enterprise level Microsoft 365 E3 or Microsoft 365 E5 plans. The important services that are included in these plans (but not the lower plans) are Azure Information Protection and Intune, both of which bring a range of security and data governance capabilities to your environment.
Recommendation
Review all your Microsoft Office 365 subscriptions and consider upgrading any that are not Microsoft 365 Business Premium, E3 or E5 so that you can take advantage of the better security and governance capabilities.
#2. What’s our Microsoft Secure Score?
Microsoft Secure Score is a rating of your organisation’s Microsoft 365 security posture, compiled from a range of configurations, metrics and various other data points, depending on what Microsoft 365 plan you subscribe to, and what services you use. The higher the number, the more secure you are.
In addition to a numeric score, the Secure Score dashboard will also provide actionable insights and prioritized recommendations tailored to your unique needs. By following these recommendations, you can progressively improve your Secure Score and strengthen the security posture of your Microsoft 365 environment to provide better protection for your confidential data.
Recommendation
Review your Secure Score and progressively implement the recommendations to improve your score.
#3. Is Multi-factor Authentication enabled on all our Microsoft 365 accounts?
Multi-factor authentication (MFA) is an authentication method that requires a user to provide two or more verification factors to prove their identity and gain access to your Microsoft 365 environment, most often a password plus a unique code provided by a separate app.
Despite being one of the most effective cybersecurity measures you can implement in your Microsoft 365 environment, MFA is not always enabled by default or enforced across all accounts. The important point to remember is that your security is only as strong as the weakest link, so for MFA to be most effective it must be enforced on all accounts in your Microsoft 365 environment, not only some of them.
Recommendation
Review all accounts in your Microsoft 365 environment and enable MFA where necessary. Configure Microsoft 365 to enforce MFA on all accounts by default.
Read more: 3 reasons you need to enable Multi-factor Authentication (MFA) today
#4. Are we using dedicated Microsoft 365 admin user accounts?
Every Microsoft 365 environment has one or more “admin” user accounts. These accounts possess elevated privileges that allow them to perform sensitive tasks such as changing system settings and accessing data anywhere across the environment. These admin privileges can be seen as the “keys to the kingdom”, and if allowed to fall into the wrong hands can be exploited to cause significant damage.
User accounts used for everyday tasks such as checking email and editing work documents should never be granted such elevated admin privileges, so as to reduce any potential harm should the account be compromised. Instead, dedicated “admin” accounts should only ever be used for duties requiring elevated security privileges.
Not only does this approach reduce the risk of accidental changes or security breaches, but it also makes it easier to monitor and audit their activities, improving accountability and traceability of any suspicious actions taken within your Microsoft 365 environment.
Recommendation
Review all user accounts in your Microsoft 365 environment for elevated admin privileges and remove such privileges in favor of dedicated admin accounts.
#5. How are we monitoring for suspicious activity within Microsoft 365?
Even with a well secured Microsoft 365 environment, ongoing monitoring and alerting of unusual activity is important for the prevention of a full-blown security incident. Monitoring can help identify a range of suspicious activities, such as multiple failed login attempts, unusual data access or transfers, and changes in user permissions. These could be signs of a brute force attack, data breach, or insider threat.
Moreover, monitoring isn’t just about detection, it’s also about response. When you spot suspicious activity, you can quickly investigate, take corrective action, and learn from the incident to strengthen your defenses.
Recommendation
Ensure monitoring is configured within your Microsoft 365 environment, and alerts are sent to the most appropriate person to take action as required.
Microsoft 365 is a highly secure platform, but that doesn’t mean that your organisation’s Microsoft 365 environment is secure by default. Microsoft provides the means, but ultimately, it’s up to you to ensure that your environment is secured appropriately, and that starts with asking the right questions.
If you have questions about your Microsoft 365 security, Grassroots IT can help. Speak with us today.
What is Cybersecurity Awareness?
Cybersecurity awareness is the level of understanding and mindfulness that people in your organisation have of the various cybersecurity threats that they may face, and how they should best respond.
A shocking 82% of all data breaches involve some human element, such as social engineering or through plain old human error and misuse. What this tells us is that people – our staff, suppliers and partners – can not only be the weakest link in our cybersecurity posture, but also offer the greatest potential to help protect against cyberattack.
Cybersecurity awareness is the lever that we must use to shift our people from being our biggest cyber-risk to being our strongest line of defence.
Why is Cybersecurity Awareness important?
With the average cost of a data breach in Australia reaching $4.4 million, cybersecurity attacks pose a very real and present threat to organisations of all types. Cybersecurity frameworks such as the ACSC Essential Eight and the NIST CSF can help us with strategies and security controls to help mitigate these risks, but technical controls can only help so far.
With the statistics clearly showing that the human element plays a major role in the effectiveness of our defences, we ignore cybersecurity awareness at our peril.
How to build a culture of cybersecurity awareness
Intentionally building any culture takes time, commitment and consistency to create and reinforce the behaviours that we wish to see in our organisation. Building a culture of cybersecurity awareness is no different.
Here are five practical ways to engage your organisation and build the cyber-aware culture you need.
Secure leadership buy-in
Culture is lead from the top and cybersecurity awareness is no different. All organisations look to their leaders to set the direction for the company not only through explicit statements, but also through implicit and implied messaging. Leaders must be seen to embrace the importance of a cybersecurity aware culture, and to lead by example.
Securing leadership buy-in can be helped by:
- Taking a holistic view of the organisation, of which a cybersecure culture is merely one piece.
- Connecting a cyber-aware culture to the company’s strategy, goals and aspirations.
- Clearly communicating the business case for strong cybersecurity awareness.
Promote robust policies, procedures and best practices
Robust cybersecurity policies and procedures are at the heart of any cyber-secure organisation. Policies and procedures must walk the fine line between protecting the organisation and being overly restrictive on how staff may go about their work. Too lenient and they may be ineffective – too stringent and staff satisfaction and productivity may suffer.
Policies and procedures should be promoted regularly to keep them top of mind with staff, along with examples of best practice responses to various likely scenarios.
Some common ways of promoting cybersecurity policies and best practices can include:
- Ensure policies and procedures are clear, actionable and easily accessible to all staff.
- Download, print and share posters and resources promoting cybersecurity best practice.
- Communicate examples of real-world cybersecurity threats, and best practice responses through internal communications channels.
Conduct regular cybersecurity training
Regular cybersecurity training will not only keep cybersecurity top of mind and reinforce best-practice threat response, but it will provide an avenue for keeping staff updated on the latest cyber-threats they may face. The challenge of course is to keep training engaging and effective.
You might like to consider these Ideas for delivering engaging cybersecurity awareness training:
- Mix up the format of delivery between online, in-person and self-paced.
- Keep training sessions short, high energy and with a clear take-away message.
- Consider bringing in an external trainer to inject new ideas and energy.
Schedule simulated cyberattacks
Research has shown simulation-based cybersecurity awareness training to be the most effective when compared to other methods such as instructor led (a close second place) and online delivery. Simulations may be run periodically to quantify the level of cybersecurity awareness in the organisation and identify improvement over time.
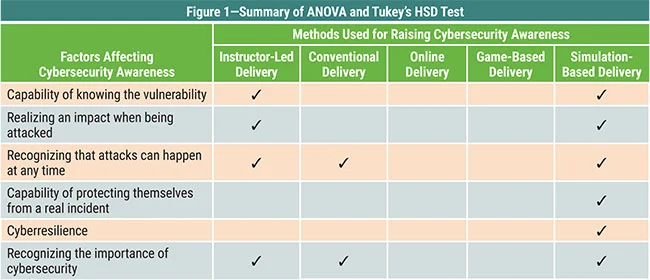
Table courtesy of ISACA.orgIn practice, the most common form of simulated cyberattack is referred to as “Friendly Phishing”, whereby staff are sent a fake phishing email to see how they respond. Those who are successfully tricked by the fake phishing email are immediately shown the error of their ways and are offered a brief online training snippet to educate them on how they could have identified the threat in time, and what a more appropriate response would have been.
Be consistent and stay informed
When impacting any organisational change, it is important to be consistent both in the message and the delivery. Be clear up front what you want your cybersecurity culture to look like and ensure that all key stakeholders are aligned and have the tools available to drive the necessary change.
Organisational culture requires ongoing stewardship. It takes time to establish the culture that you want, and ongoing vigilance to keep it strong. Maintaining an effective culture of cybersecurity awareness is an ongoing process, not a once-off activity
Conclusion
Cybersecurity awareness presents both the biggest threat and the largest opportunity to your organisation’s cybersecurity posture. A poor level of awareness will leave you exposed to attack, regardless of what technical security measures you may have in place. A culture of high cybersecurity awareness on the other hand will be your strongest line of defence in protecting your company.
Effective cybersecurity is as much about policy & governance as it is about tools and technology, however knowing where to start with these things can be challenging. In this post we have compiled a list of useful cybersecurity policy resources to help you build and enhance your cybersecurity governance.
Australian Cyber Security Centre
The Australian Cyber Security Centre (ACSC) is an initiative of the Australian government’s Australian Signals Directorate. The website contains a wealth of resources for both individuals and organisations, including alerts for new security threats, and the ability to report a cybercrime or security incident.
Essential Eight Maturity Model
The Australian Cyber Security Centre (ACSC) has developed extensive strategies for the mitigation of cyber security incidents, with the most effective of these labelled The Essential Eight. Not only is the Essential Eight an excellent initiative for every business, Essential Eight compliance is also fast becoming a mandatory requirement for many tenders, contracts and cybersecurity policies.
Essential Eight Maturity Model | Cyber.gov.au
Key questions for an organisation’s board of directors
The Australian Securities & Investment Commission has compiled a list of key questions for board members to consider. Topics include Risk management framework, Identifying cyber risk and incident response awareness.
Key questions for an organisation’s board of directors | ASIC
Create a cybersecurity policy
The Australian government Business website provides an excellent quick-start guide to creating your own cybersecurity policy. Of course every policy will be unique to your own organisation, but this guide provides an excellent template to get you started, including sections such as:
- Password requirements
- Social media access
- Incident response planning
Create a cyber security policy | business.gov.au
University of Queensland Cyber Security Policy
The University of Queensland has published its own Cyber Security Policy which provides an interesting real-world example of such a policy. Although of course uniquely crafted for the university’s own purpose, it does provide a useful example of how such a policy can be shaped.


