Microsoft 365 has many security features and capabilities built in, however with a few simple steps you can improve your Microsoft 365 security and greatly increase your cybersecurity stance with some easy changes to system configuration and business practices.
#1. Enable Multi-Factor Authentication
Multi-Factor Authentication is by far one of the most effective ways to improve Microsoft 365 security and protect accounts from being hacked. When you have multi-factor authentication in place, your employees will be required to enter in a unique, constantly changing code along with their usual username and password in order to log on to their Microsoft 365 account. Even better, Microsoft 365 has some super clever features that mean you will not be constantly prompted for this code if you are connecting from a trusted location or device.
Using Multi-Factor Authentication ensures that your valuable data doesn’t get compromised should your employees use easy-to-guess passwords or leave the password written down out in the open. While it’s important to use strong passwords, this second step ensures that a malicious party won’t be able to gain access as they would need the employee’s phone as well.
#2. Use dedicated admin accounts
Your admin accounts come with elevated privileges, options, and security features. The people who use these accounts can grant rights to other users, install software, and more. This makes them a prime target for cybercriminals and hackers. Each administrator should have their own account, and they should have a separate user account for non-admin tasks.
Every admin account should have multi-factor authentication equipped. You should also routinely monitor these admin accounts to ensure they’re not granting unauthorised privileges to users who don’t need them because this increases your security risks. When an admin leaves the business, immediately shut down their admin account so they can’t use it against the business.
#3. Educate your staff to be cyber-safe
The Harvard Kennedy School has an excellent handbook to assist you in training your staff on cybersecurity called the Cybersecurity Campaign Handbook. This book can help you set up a culture of cybersecurity awareness that your staff can use from the moment you hire them. You’ll train your users to identify phishing attacks through their emails to keep hackers out.
Your staff should know what a strong password is, and how to set them up, how to protect their devices and how to enable security features on Mac PCs and Windows 10. Giving your staff ongoing training allows them to keep up with the latest threats.
#4. Protect against ransomware attacks with mail flow rules
Ransomware is a program that restricts an infected computer’s access to data by locking the computer or encrypting the data. Once you get locked out of the computer, it usually asks for a “ransom” to extort money out of the victims. This money is typically cryptocurrency like Bitcoin, and the hackers claim they’ll give you access back to your computer once they get the money.
You can create mail flows that block any file extensions that cybercriminals commonly used for ransomware. You can either block all file types that could contain malicious code or ransomware, or you could set up a rule that warns your staff that they’re about to open an Office file attachment that has macros.
#5. Raise your malware protection levels
Malware is an umbrella term that covers many types of software that purposely damage a computer. Malware can be Trojans, viruses, spyware, ransomware, or worms. Malware is short for “malicious software,” and training your staff on avoiding it is critical.
Luckily, Microsoft 365 comes with built-in protection against this form of cyber attack. You can enhance this protection by automatically blocking file types or attachments that cybercriminals commonly use for malware.
#6. Set up Office message encryption
Encryption adds another layer of protection to any messages you send both inside and outside of your organisation. This way, if a staff member accidentally types in the wrong email and sends it to an unintended party, they can’t pass it around. The encryption lets only the intended party see the email when they open it.
You can have your staff use the “Do not forward” or the “Encrypt” prompt each time they send an email. Encryption comes built into Office 365, and it works with Yahoo!, Outlook.com, Gmail and other email providers.
#7. Disable the ability to auto-forward emails
Your emails are a vulnerable point for your organisation, especially if your staff have a habit of forwarding them. Any hacker that gains access to your staff’s inboxes can configure the inbox to automatically forward mail. When they do, they can attach Malware to the email and spread it throughout the organisation.
The first step you take is to make sure your staff aren’t forwarding emails on their own. You can set up a mail flow rule that prevents auto-forwarding emails from external senders. This way, even if a hacker does get in, they won’t be able to infect the entire system.
Your staff will routinely receive, share, and send attachments like spreadsheets and presentations. It’s very difficult to tell which attachments are safe to open and which ones are infected with malware.
Some Microsoft 365 plans come equipped with Advanced Threat Protection built-in. This suite includes ATP Safe Attachment protection. You have to enable it and set up a new rule for it. However, it can protect your staff from spreading malicious software through attachments.
#8. Defend your email from phishing
You can configure anti-phishing protection in both Office 365 or Microsoft 365. You can set up a policy to protect your custom domain and your staff. This software protects your organisation from general phishing attacks and malicious impersonation-based phishing attacks. Hackers won’t be able to send impersonation emails from any user you have listed in your custom domain.
Speak with the Office 365 security experts
Grassroots IT are the Microsoft Office 365 security experts, keeping our clients cyber safe in Brisbane and across Australia since 2005. One thing we understand about Microsoft 365 security and compliance is that unless you work with these tools every day, it can be hard to “know what you don’t know”. For that reason, we created our Microsoft 365 Security & Compliance Packs – simple, fixed-price packs to help you take advantage of all of the advanced security and compliance features in Microsoft 365, without the complication of drawn out project scoping and design. Contact us today to learn more.
Cyber-security threats and data breaches are becoming increasingly rampant, sophisticated and difficult to mitigate. Statistics from the latest Australian Cyber Security Centre Threat Report show that instances of malware attacks, data breaches, and intrusion attempts are on the rise. The challenge of ensuring cybersecurity is a global issue affecting many industries and organisations.
Find out the difference in our new video
In years gone by, we may have thought the chance of experiencing a cybersecurity breach was pretty low but, these days, the more aware business leaders talk not about the possibility but of when a cyberattack will happen. So let’s talk about how can we take preventative action to defend our computer systems and keep the risk of an attack to a minimum.
In this digital age where almost everything can be found online and in the cloud, malicious attackers have a much wider window of opportunity to conduct their mischievous agendas. Businesses are becoming more and more familiar with cyber security breaches and the associated damage and downtime which impacts those attacked.
For the first half of 2019 alone, over forty organisations in Australia reported data breaches (source: webberinsurance.com.au) and they are just the cases officially reported. One report gathered from the quarterly statistics report of the Office of the Australian Information Commissioner (OAIC) showed a staggering ten million people affected by a single data breach incident that happened this year. On average, the OAIC received around 72 notifications of data breach reports per month from January to March 2019. That is contact information, financial details, personal identification, health information and more sensitive data being passed around the dark web unbeknownst to its users.
Many cyber security defences set up for businesses are primarily focused on protecting high profile accounts, but what is often overlooked is that cyber attacks have evolved over the years and the attackers have become more patient and strategic with their actions. Often they begin by targeting the more vulnerable and least protected profiles. From there, they penetrate upward into the organisation’s core data and before you know it, you’ve lost vital information just by leaving the backdoor open.
With the advancement in technology and the evolution of cyber attacks, cyber security is no longer optional – it is now a necessary part of building and maintaining a long-running, secure business.
First Line of Defence: Firewalls
One of the primary ways of defending our computer systems is through the use of firewalls.
What is a firewall? In order to use programs and apps that connect to the cloud, we need to be able to access the public internet from our private network. Firewalls block access to or from our private networks from unauthorized web users or illicit software while we’re connected to the Internet. A firewall may be implemented using hardware, software, or a combination of both.
Routers can provide some basic firewall services, but only offer minimal defence. As cyber criminals improve their strategies in conducting their attacks, the development and usage of firewalls has also needed to evolve. Enter the intelligent unified threat management firewall.
What is an Intelligent Firewall and how is it different from the usual firewall?
An intelligent firewall is similar to an ordinary router but it does more than basic firewalling. It works through your Internet traffic to filter, scan and look for potentially malicious activities going on in the background and sends out alerts to let you know about threats coming into your network so you can immediately diagnose the problem.
It also has the ability to enforce internal policies like preventing your staff from browsing and accessing potentially harmful or inappropriate websites at work. With the evolution of AI, some manufacturers are even using deep learning in their machines to track historical attacks to automatically prevent similar actions in the future.
How do I know if I have an intelligent firewall?
The simplest way to learn if you do have an intelligent firewall in place is to ask your IT partner.
You can also look for some of the most trusted names when it comes to intelligent firewall devices. Here are some of the vendors that are known to do an extremely great job of securing your business network through the use of intelligent firewall appliances:

One of the top picks when it comes to endpoint protection. This award-winning vendor incorporates artificial intelligence and Endpoint Detection Response (EDR) technologies to provide a smart and reliable defence line for your network.
Created by the leading network device manufacturer Cisco, Meraki pushes simplicity and Cisco technologies forward to provide a rich and seamless experience to newer generations. By utilising the cloud with wireless connections, Meraki promotes a more convenient approach to network management while ensuring the security of data within a wireless network.

Sonicwall has a broad range of products from hardware to other services to provide effective network security, control and visibility. It also integrates deep learning to be able to prevent repetitive intrusions to the network.

Costs and Benefits
Having an intelligent firewall will involve more costs than relying on a basic router, but also provides significantly more protection. An intelligent firewall is more than just a physical device. With the constant evolution and increasing sophistication of cyber attacks, an intelligent firewall needs to be connected to its vendor platform to deliver the latest updates, AI rules and knowledge in order to stay ahead of the game and continuously provide you reliable security services.
Having a strong firewall protecting your network should not be considered optional in this day and age. With technology progressing so quickly and as we become more and more reliant on the internet to access our business systems, it’s imperative to have a solid layer of defence protecting your business data.
Now that you understand what an intelligent firewall is and its importance, start talking to your trusted IT partner to discuss the right firewall options for your business network. Seek the help of someone who can help you align your business goals and IT budget with your network security plan to ensure your business is well defended from cyberattacks.
This article is part of a cyber security series by Grassroots IT and The Power Up Project podcast.
Back to more news, updates and resources or learn more about Cybersecurity
What is phishing?
Phishing is a form of cyberattack whereby fake emails are sent to your staff with the intention of tricking them into sharing password details, granting access to a secure system, or otherwise taking some action to benefit the cybercriminal. Of the various types of cyberthreat that your organisation is likely to experience, phishing will be the most common, making it vital that you can quickly identify a phishing email.
Ideally you will have security systems in place, such as good email filtering, to ensure that phishing emails are blocked before even reaching your inbox. Unfortunately, even with good security systems in place, it’s not uncommon for the occasional phishing email to slip through.
With the average cost of a data breach in Australian now at $4.4 million, and over 82% of all data breaches involving some form of ‘human element’ (such as accidentally engaging with a phishing email), you can see why it’s important to be able to identify a phishing email, and to know how to respond safely.
What are the different types of phishing?
Over the last few years several distinct types of phishing attack have emerged. They all have the same ultimate intent but take slightly different approaches to achieving it.
Phishing
The most common form of phishing attack involves the cybercriminals casting a wide net, with fake emails sent indiscriminately and often in huge numbers. These emails are generally not targeted to their recipients in any meaningful way, apart from pretending to be from well-known brands that the recipient is likely to have some level of trust in, such as Commonwealth Bank or Microsoft. Phishing emails seek to trick the recipient into either sharing personal data or installing malicious software onto their computer to enable further attack.
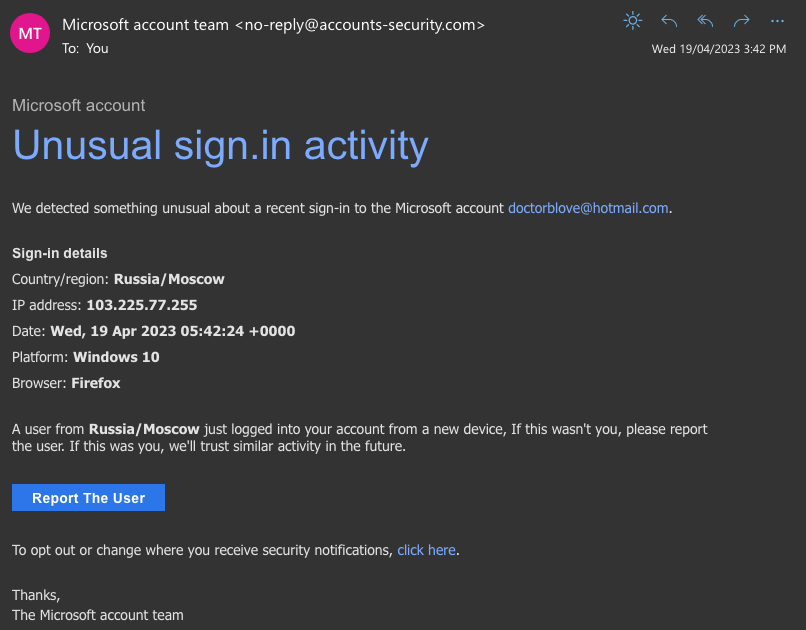
Spear Phishing
Spear phishing is similar to standard phishing, with the one difference being that spear phishing is targeted at and personalised for specific individuals. This requires the attackers to have some personally identifiable information on their victims, such as email address, first and last names and job title.
This slightly more sophisticated form of attack takes more time to craft and will therefore generally target victims with a higher perceived value, such as more senior staff or those likely to have access to higher value systems.
Whaling
Whaling is a further evolution of spear phishing, targeting senior executives and others in privileged positions. Whaling emails are individually crafted based on specific knowledge of the target organisation and key individuals, and often play on the pretext of a busy executive asking for some information or action to be taken urgently (such as the transfer of funds to a specific bank account).
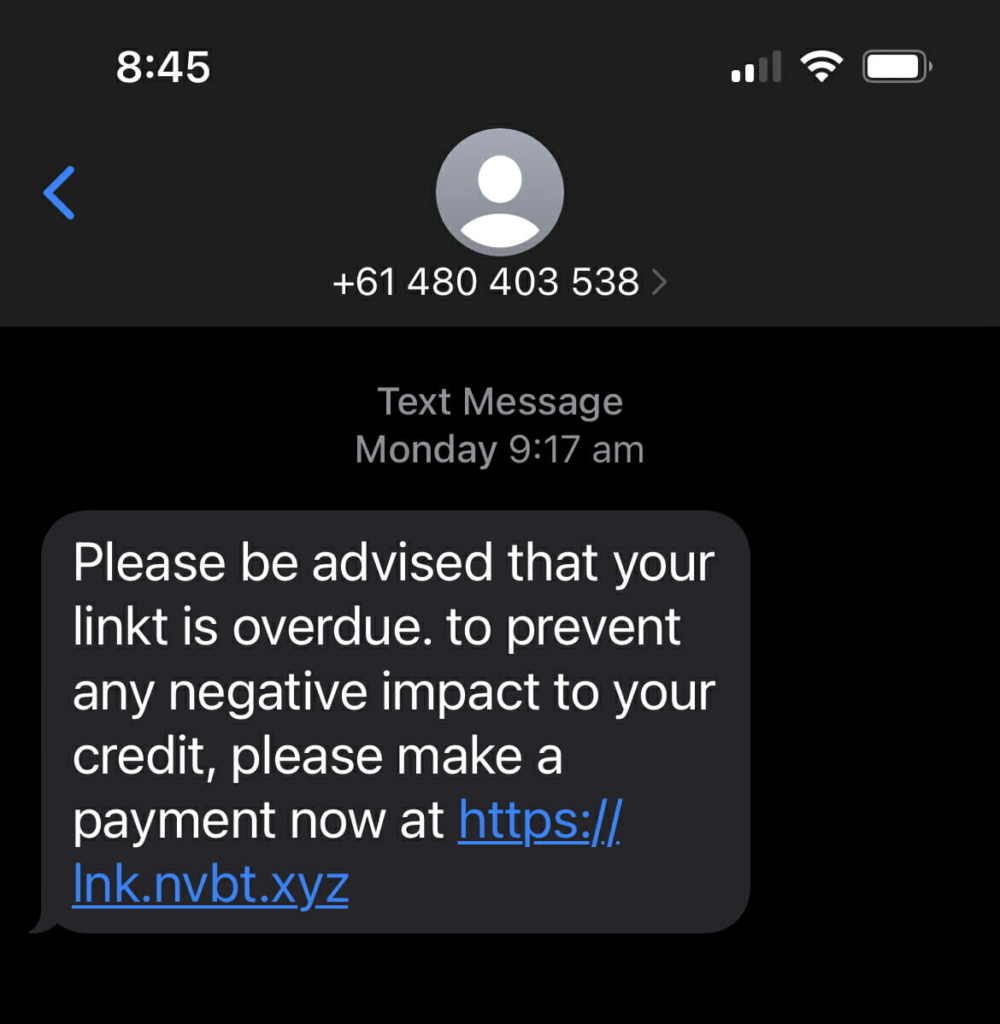
Smishing
Smishing is a variant of phishing that uses SMS messages rather than emails to trick the recipient into clicking on a fake link and sharing personal data. Common examples in Australia may pretend to be from familiar brands such as Australia Post and Linkt.
Why is email phishing so common?
Of all the different types of cyberattack, why is phishing so prevalent? First is the fact that phishing attacks can be extremely cheap and easy to execute. Email use is extremely commonplace, providing a vast audience of potential targets, while the tools required to execute an attack can be obtained cheaply and easily on the dark web.
The second key point is that humans are – well – human. We can be extremely susceptible to influence through common psychological techniques, such as our tendency to follow rules. We also tend to make mistakes, many of which pass without consequence, but some (such as clicking on the wrong email link) may not.
We can also add that at an organisational level there is often a lack of cybersecurity awareness, meaning staff simply do not recognise a phishing email, nor do they know how to safely respond when they do
Read more: Building a culture of cybersecurity awareness in your business
How to identify a phishing email
To protect against a phishing attack, it’s extremely important that you be able to identify a phishing email so that you can delete it safely, and not accidentally fall prey. The good news is that there are some common identifiers that you can look out for. After just a little bit of practice you will quickly recognise a malicious phishing email without a second thought.
Unfamiliar sender
Phishing emails will often purport to come from either a generic corporate sender, or a person that you are unfamiliar with. This isn’t to say that you won’t ever receive legitimate email from an unfamiliar sender, but when you do, be cautious to validate it carefully.
Generic greetings
Given that most attackers will not have any personal information about you beyond your email address, phishing emails are likely to use generic greetings such as “Dear Sir”, rather than identifying you by name.
Urgent call to action
Phishing emails often convey a sense of urgency, encouraging you to ‘click now’ to claim a reward or avoid a penalty.
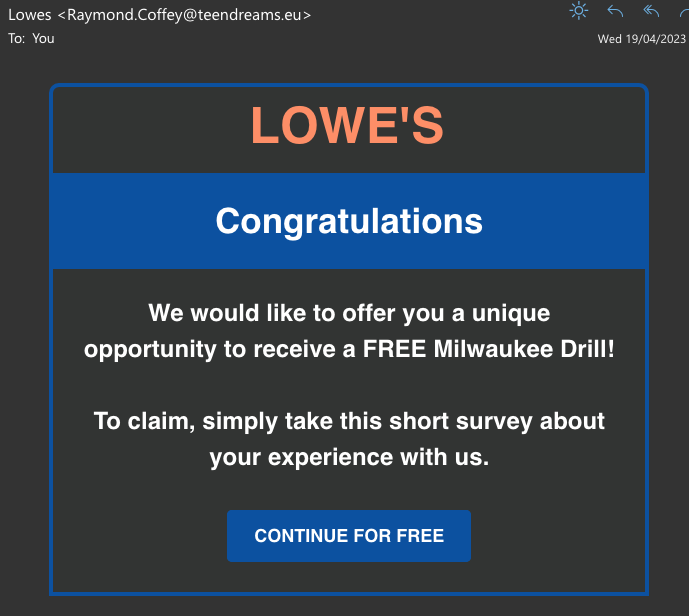
Too good to be true
Phishing emails may contain an offer that’s too good to be true. How likely is it that your long lost (and forgotten) great-aunt has died and left you a million dollars?
Bad spelling & grammar
Phishing emails often contain bad spelling and grammar, something you’re unlikely to see from a legitimate, professional organisation. This poor use of language may be due to an amateur translation from a foreign language, or it may be intentional in an attempt to avoid email filters.
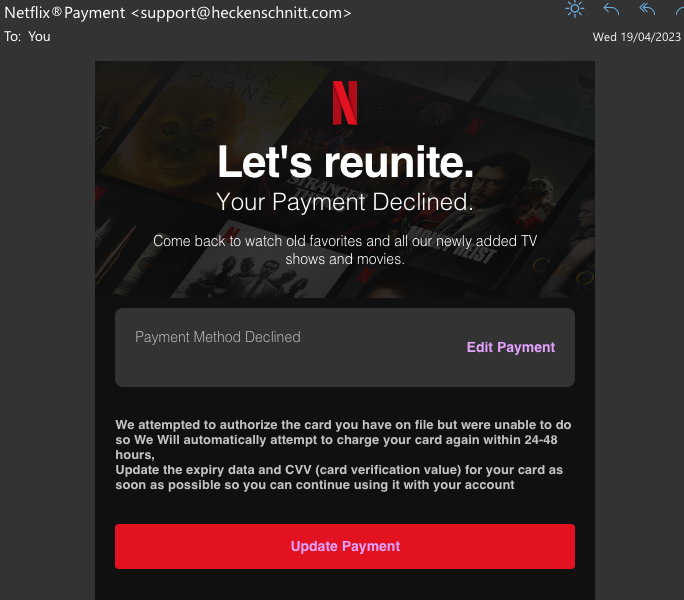
Request for sensitive information
Many phishing attacks will try to get personal information from you, such as passwords or credit card details. Legitimate organisations will never ask for such information via email.
Inconsistencies in email addresses, links & domain names
All legitimate organisations have their own domain name, such as “grassrootsit.com.au” which they will use for their website and their email addresses. Capitalisation of domain names isn’t important; however, all other spelling and punctuation is. Phishing email will often come from email addresses that clearly don’t use the purported organisation’s domain name, or in some more sophisticated phishing attacks may use a domain name that closely matches the legitimate one, but with a sneaky minor change.
Suspicious links
As with email addresses, any links offered in a legitimate email should use the sending organisation’s proper domain name. Check all links carefully before clicking them to ensure that they do in fact use the correct and legitimate domain name. You can check the link address by hovering your mouse curser over the link without clicking.
Unexpected attachments
Always be suspicious of attachments on emails that you weren’t expecting, especially when the email is from an unfamiliar sender. Email attachments are an effective way for attackers to infect your computer with malicious software, but that can only happen if you open the attachment.
What to do if you receive a phishing email
Once you’re familiar with the common tell-tale signs of a phishing email, it will be clear as day when you next receive one. What you do next is crucially important.
The most important thing to remember is to not click on any links or attachments in the email, and to immediately delete the email. Some organisations may ask staff to report any phishing emails to their IT department, in which case you should follow the process provided and do so.
If you do accidentally click on either a link or an attachment in a phishing email, notify your IT department immediately and follow their instructions. There is a good chance that no harm has been done, but it is better to be safe than sorry.
Phishing is the most common form of cyberattack that you are likely to experience, but with a little knowledge it’s easy to identify a phishing email and take appropriate steps to avoid a security incident.
mation from you, such as passwords or credit card details. Legitimate organisations will never ask for such information via email.
If you are using one of the major Software as a Service Offerings (SAAS), such as Office 365 or public cloud file storage, then you are benefitting from incredible economies of scale. Your data is highly available and accessible from almost anywhere securely.
So, you may be thinking…
“All of my stuff is in the cloud. It’s safe!“
But the thing is, this doesn’t necessarily mean that your data is backed up in such a way that you can recover it on-demand.
It’s a common misconception that your data in SaaS applications is fully backed up. For a service to be highly available and resilient, as guaranteed in service levels and expected by the modern workplace, Cloud vendors layer on security and redundancy. Your data is almost definitely backed up by the vendor in the sense that it lives in different parts of the data centre, possibly even in different states, and this makes it highly resilient. But, this is for their benefit. It doesn’t necessarily mean that you are able to roll back and recover data that is lost for whatever reason.
“How can I lose my data?”
Here are three ways that the unthinkable might just happen:
1. Accidental Deletion
Data loss can be the result of human interaction pre-caffeination. Quite simply, it can be caused by human error as simple as someone accidentally hitting that big dirty delete button. Human error is by far the most common cause for data deletion and also potentially the most dangerous because it may not be discovered for some time – longer than many traditional backup regimes accommodate for.
2. Overwriting Data
As well as files being accidentally deleted, information can also be unknowingly overwritten by both users and third-party applications. Many systems hold large volumes of data. Living data that is constantly added to and updated. Bulk uploads, mass importation of large data sets by integrated third-party applications which manage the data inside your applications. Not everything is always operating as it should.
3.Malicious Action
International espionage may seem far-fetched for your company’s cloud data so let’s leave aside the black hoody wearing hacker boogey man, surpassing security systems to delete and corrupt your data complete with retro 90s soundtrack. One of the benefits of having data stored in a cloud system is the increased levels of security that the sheer scale of resources permits. If a nefarious user were able to break through the significant defenses in Microsoft world, it would make more than a ripple in the news.
A far more likely scenario would be the disgruntled employee. When employees leave, be it under a less than ideal circumstance or not, they may delete important information. You want a solution that enables you to easily restore deleted data.
Additionally, you want a system that lets you easily access the information that former employees have left behind in their inbox and My Documents folder without having to pay for their seat license. Many organisations are still retaining the accounts of departed employees in order to ensure that critical data, mail and documents are safely retained and not lost. This is obviously not the best use of scarce resources.
Regardless of how data is lost, it can happen. It’s important that you know that Office 365 doesn’t back up anything long term. If you delete something, after a 30-day period it is gone forever.
Microsoft 365 backup solutions can fill a gap in the Office 365 offering by backing up the data in your mailboxes, One Drive and SharePoint sites.
Cloud Backup Solutions can offer unlimited retention and could be an effective way to not only insure your business against the risk of data loss but also provide you with some very useful features. They allow you to restore your data at a granular level. Individual files or emails can be recovered directly to your computer. This is a unique and very handy capability not available in other products.
An easy-to-use dashboard gives you the ability to view and manage your backups, use robust search capabilities to target specific emails or files and either restore them to a user’s account or, as a very handy bonus feature, download them directly to your computer.
Whether you have a rogue employee deleting files, accidental user error or ransomware attacks, it’s important to know that there are solutions available to protect you from these risks and keep your data safe.
Talk to us today about the data-saving solution that is right for your business.
Securing critical business systems from cyber-attack can be a complex task, with a seemingly endless array of methods available to choose from, each with pros and cons. To help focus our efforts there are various cybersecurity models and frameworks available such as The Essential Eight Maturity Model and the NIST Cybersecurity Framework, both of which offer excellent guidance on improving your cybersecurity posture.
Irrespective of which cybersecurity framework you choose, and which strategies you decide to pursue, there is one cybersecurity control that should be a no-brainer in every organisation, and that’s Multi-factor Authentication.
What is multi-factor authentication?
Multi-factor authentication is an authentication method that requires a user to provide two or more verification factors in order to prove their identity, and gain access to a secure system. In many cases this will mean the user providing their usual password along with some other unique and verifiable piece of information.
There are three main forms of multi-factor authentication in common use:
- Unique code: In addition to their password the user will be prompted to enter a unique code that they obtain either via a text message, or via an authentication app installed on their smartphone. These codes are valid only for a very short duration, often 60 seconds, before a fresh code is required to successfully complete authentication.
- Authentication app: When the user attempts to logon to a secure system with their username and password, a prompt will appear on a special authentication app installed on their smartphone. They then simply tap to accept the prompt, and authentication will proceed.
- Biometric: Every one of us has unique and verifiable biometric features, such as our fingerprints and facial appearance. These unique features can be scanned and used as a second authentication factor.
Why you should enable multi-factor authentication whenever possible
Unfortunately, multi-factor authentication isn’t always enabled by default on the systems that you use, even though it most likely is available as a feature. Until you actively choose to enable MFA on each system that you use, you won’t receive the extra value that it offers, leaving critical business systems potentially exposed to cyber-attack.
So, what are the top 3 reasons to enable MFA?
#1 – MFA protects accounts from unauthorized access
The traditional approach of only requiring a username and password to logon to a secure system is unfortunately not actually very secure, particularly as cyber-criminals become increasingly more determined.
Usernames are often easy to discover, often just being the user’s email address. Passwords can be hard to remember, particularly with so many different systems and passwords to keep track of, so people tend to pick simple ones, or use the same password on many different systems, all of which makes them easier to crack.
Multi-factor authentication on the other hand is extremely effective at protecting user accounts from unauthorised access. This is why most online services make MFA available, and why many such as banks have made MFA compulsory. Even if a cyber-criminal were to obtain your username and password, without access to your second authentication factor they would still not be able to access your user account.
#2 – MFA can enhance the user experience
Multi-factor authentication offers several opportunities to enhance the user experience and, in the process, improve productivity, efficiency and user satisfaction. Single sign-on services that user multi-factor authentication allow users to sign-on once, and then be automatically and securely authenticated into multiple other systems, negating the need for them to sign-on to each system individually.
Biometric multi-factor authentication can alleviate the need to manually enter any authentication details at all. A single fingerprint touch, or a glance at the camera in your laptop can be sufficient to securely login.
Finally, contrary to long held wisdom, the current guidance from security experts such as Microsoft and the NIST is to not force users to change their password periodically, but instead to let them keep the same password indefinitely – on the condition that the password chosen is long, complex, and multi-factor authentication is in use.
#3 – MFA can help comply with standards & regulations
As many organisations seek to push cybersecurity compliance down through their supply chains, demonstrating the maturity of organisational cybersecurity is rapidly becoming a requirement for many government and commercial dealings.
Aligning with a broadly recognised cybersecurity framework such as The Essential Eight or the NIST is an effective and widely adopted approach to not only improving cybersecurity posture, but also being able to demonstrate that maturity to partner organisations when required.
Multi-factor authentication is identified as an essential security control in not only the major cybersecurity frameworks, but also directly in many commercial engagements such as cyber-insurance policies.
Watch our free on-demand webinar now: The Essential Eight Cybersecurity Maturity Model
Conclusion
Multi-factor authentication should be a non-negotiable requirement in every organisation’s cybersecurity strategy. Not only does it provide an effective layer of protection against user account breach, but it can enhance user experience and productivity, while also helping to align the organisation with widely recognised cybersecurity standards.
As the new Notifiable Data Breach Schemecomes into effect in Australia as of 22 February 2018, there is now an onus on business to protect and notify individuals whose personal information is involved in a data breach that is likely to result in serious harm.
When most people think of data breaches, they think of sneaky virus attacks with employees being tricked into opening files allowing viruses to penetrate servers, but the reality can be much more mundane, plausible and preventable.
And it’s not all about IT systems and cybersecurity. There have been numerous cases of hard copy records being disposed of inappropriately, sensitive data on USBs lost on the way home or machines being disposed of complete with data on the hard disk. (As a side note, did you know that GrassrootsIT offers a service where your decommissioned hardware is disposed of securely?)
Who is covered by the data breach scheme?
The Notifiable Data Breach (NDB) Scheme affects organisations covered by the Privacy Act – that is, organisations with an annual turnover of $3 million or more. But, if your business is ‘related to’ another business covered by the Privacy Act, or deals with health records (including gyms, child care centres, natural health providers, etc.,), or is a credit provider, then your business is also affected.
What do you need to do?
Complying with these new laws means more than ringing the bell and notifying your customers and authorities when a breach occurs. Organisations are required to take all reasonable steps to prevent a breach occurring in the first place. This means putting in place the systems and procedures to identify and assess breaches and issue a notification if a breach is likely to cause ‘serious harm’.
How do you assess your risk?
The Privacy Act already requires organisations to take all reasonable steps to protect personal information. The new data breach laws merely add an additional layer to assess breaches and notify where the breach poses a threat.
- Firstly, consider some of the following questions:
- How does personal information flow into and out of your business?
- What information do you gather?
- What information do you provide?
- Where do you store private information? – What systems do you use, where do these systems store data, what level of security is provided within those systems and what level of access does each team member have (and should they have access for their role)?
- Who in your organisation has access to sensitive information, and not just who is accessing the information for their work but who ‘could’ access this information?
- What are the possible impacts on an individual’s privacy?
- What are the policies and procedures in place to manage private information, including risk management and mitigation, are these adhered to and actively managed?
- Do you have a policy review process, and if so, is it reviewed at least annually, and also with the introduction of new systems and technology? (Remember, you can’t just have a policy sitting somewhere, it needs to be actively reinforced and adopted by team members)
- Protect your business. Document, document, document! If there is ever an issue where your business’ culpability is assessed, your capacity to prove that you took all reasonable steps will be important.
What is your Data Breach Plan?
When it comes to data breaches, all organisations must have a data breach response plan.
The data breach plan covers the:
- Actions to be taken if a breach is suspected, discovered or reported by a staff member, including when it is to be escalated to the response team.
- Members of your data breach response team (response team), and;
- Actions the response team is expected to take.
Hopefully all the systems you have in place will ensure you don’t need to deal with a data breach, but if it does happen, you will need to notify various parties, including:
- The individuals impacted by the data breach
- The Office of the Australian Information Commissioner
You can notify the Commissioner using this form.
To access the full guide to the Notifiable Data Breach Scheme, you can find it on the OAIC website.
While it’s unknown at this stage what the repercussions will be from a data breach and how the OAIC will police it, it’s important that we get our preparation in place. At the end of the day, making sure we have robust systems to protect the data of our clients should be high on the priority list anyway – this is just another reminder to ensure we have the right policies and procedures in place to back up what we’re already doing.
If you need any assistance assessing the security of your IT systems, contact us today.
In just the last five years, business leaders have changed the tone of their cyber security conversations. It is no longer a discussion about layers of defence or the beefiness of the firewall, instead Directors now understand it’s no longer a matter of ‘if’ but instead a matter of ‘when’ the system will be breached. And the smart companies have already started to shift their resources from preventative techniques to detective ones.
The fact that historical approaches to cybersecurity are no longer good enough is an indication that cyber attackers have become more intelligent and patient, and that the nature of the attacks are more sophisticated. In today’s digital world, this is something business leaders have come to accept.
The perimeter of your network can no longer be defined and effectively controlled, instead attackers have learned to be patient and exploit lower risk vulnerabilities that are usually ignored by internal IT teams, allowing exploits to go unnoticed.
This demonstrates all the more reason Australian businesses need to take cyber security more seriously. The first step will be to focus on predicting where the next risks will be for their business and working pre-emptively to come up with solutions.
There is no better way to demonstrate the urgency of developing formal cyber security plans for your business than looking at some of the big players and the cost of their data breaches:
Case Study 1 – Target
The brand we know and love, Target was subjected to a malware based attack through a compromised point of sale system that allowed hackers to steal credit card information of customers for three years without detection. Target’s share prices dropped 13.7% the month of announcing the data breach, and said the cost of the breach aftermath was close to $163 million.
Case Study 2 – Sony Pictures
This time hackers used more complex exploits. They utilised highly sophisticated phishing, calling employees pretending to be from internal IT teams, and ended up creating fake digital authentication certificates to bypass security systems. The breach allowed the hackers to expose the entire Sony employee email servers to the public. Sony admitted the cost of the IT repairs after the breach totalled $35 million, with the total cost of the breach coming close to $1 billion.
Case Study 3 – US Office of Personnel Management
Government departments are especially vulnerable which is why the Coalition has recently introduced an Australian Government Cyber Security Strategy. In the United States, however, the Office of Personnel Management had 22 million government employee records stolen by a contractor who was tasked with performing background checks. The information stolen included employee driver’s licences and passport information.
Case Study 4 – Yahoo
One of the largest breaches of customer information ever recorded, Yahoo reported in late 2016 that a breach occurred three years earlier in 2013 of over 1 billion user accounts that were compromised by hackers. The cyber criminals took and published the user records which included full names, emails, data of births, secret questions and answers and passwords. Verizon Communications reduced its original take-over bid of Yahoo by $925 million as a result of this breach, with the real implicated cost of the breach not disclosed, the catastrophic effect of the breach has certainly been felt in the reputational damage Yahoo has faced in the media.
So how can my company be compromised?
This is question most want answered. How can I be breached? With the premise of the question being ‘what can I do to prevent this particular breach?’ The reality is, for close to 60% of cases, attackers will be able to compromise an unprepared organisation within minutes.
Between 70-90% of malware samples were uniquely created to an organisation. This means attackers will likely evaluate your specific business, looking closely at the applications you are running to develop a unique exploit.
The prevalence of phishing is also a very high risk. Two thirds of incidents where a business was compromised included a pattern of phishing. In a recent study by the Ponemon Institute, 23% of business employees open phishing messages and 11% click on attachments within the first hour of receiving them.
What will a cyber breach cost?
Perhaps you’re not in the middle of a take-over bid, but the cost of cyber breaches will still be great. IBM interviewed 1500 organisations and found that the data breach cost per record (that is, think how many paying customers you have ever had in your company records) would amount to between $200-400 per customer. And the costs are growing. You need to consider not only the IT repair and hardware costs, but the reputational damage that will inevitably occur when you are forced to publically disclose your company was breached by the Privacy Commissioner (and the cost of fines if you don’t).
Where should I focus if I want to protect my business?
Start by assessing the cyber risks that apply to your business. Look at your cyber maturity and your business objectives:
- What digital solutions are changing in line with where the business is heading?
- Consider how you will mitigate those risks, what is your ‘plan b’ and ‘failsafe’ for each critical system?
- What type of cyber awareness training might be appropriate for your employees and how regularly should they refresh their knowledge?
- Ensure you have senior management support for good cyber practices and that is reflected through the company culture.
- Ensure you have three lines of defence for critical systems:
- the right configurations,
- effective and regular monitoring of those controls and configurations, and;
- having an independent expert regularly audit and assess those controls to determine any weaknesses.
Cyber threats will continue to rapidly evolve in the years to come. It is now more critical than ever to ensure you remain a step ahead of cyber criminals and your competitors to give your company the edge to grow and succeed securely.
References:
https://techcrunch.com/2015/02/25/target-says-credit-card-data-breach-cost-it-162m-in-2013-14/
http://www.csoonline.com/article/2879444/data-breach/hack-to-cost-sony-35-million-in-it-repairs.html
https://cybersecuritystrategy.dpmc.gov.au/assets/img/PMC-Cyber-Strategy.pdf
http://fortune.com/2017/01/09/yahoo-marissa-mayer-board-verizon-acquisition/
Cost of Data Breach Study: United States, Ponemon Institute LLC, May 2016.
https://www-03.ibm.com/security/infographics/data-breach/
This is a guest post by Gavin McDowell, Chief Security Officer at Gridware Cybersecurity. Gavin is a highly experienced information security expert with over 17 years experience in the IT industry. Gavin McDowell is the Chief Security Officer at Gridware Cybersecurity. Gavin is a highly experienced information security expert with over 17 years experience in the IT industry. Prior to Gridware, Gavin held several senior security roles at Accenture Consulting, Symantec Australia and Westpac Banking Corporation. Gavin has a Bachelor of Computer Science (First Class Honours) from the University of Sydney and a Masters of Business Administration from Macquarie Graduate School of Management.