Are you unknowingly overspending on your Microsoft 365 licences? You’re not alone. But the impact of poor licence management goes far beyond just your bottom line.
As IT professionals, we’ve observed that licence management is often overlooked, despite its significant impact on a company’s operational efficiency, security posture, and overall productivity. Let’s explore why this matters and how proper management can benefit your business.
Common Ways Businesses Mismanage Microsoft 365 Licences
Here are 4 common ways businesses mismanage their Microsoft 365 licences:
- Retaining inactive licences: Licenses can easily remain assigned to former employees or unused accounts. Beyond the obvious cost implications, this poses a significant security risk, potentially leaving access points open to unauthorised use.
- Incorrect licence mix: Not all licences are created equal. An imbalanced mix can lead to overpayment or lack of crucial features, impacting costs, productivity, and your ability to implement critical security measures. .
- Overprovisioning features: Many staff members are assigned comprehensive licences when they only require basic functionalities. This not only results in unnecessary expenditure but can also overwhelm users with unused features, potentially reducing productivity.
- Neglecting regular reviews: Microsoft frequently updates their offerings. Without regular reviews, you may miss out on new features or security enhancements that could significantly benefit your business operations.
Why Effective Licence Management Matters
It’s crucial to understand that effective licence management isn’t just about minimising costs. It’s about optimising your Microsoft 365 environment to align with your business needs and strategic goals. Here’s why it truly matters:
- Enhanced Security: Proper licence management ensures you have access to the latest security features, reducing your organisation’s vulnerability to cyber threats. We recommend the Microsoft Business Premium plan as the sweet spot for both price and features, particularly around security & compliance
- Improved Compliance: Certain licence types include advanced compliance tools. Having the right licences helps you meet regulatory requirements more effectively. For example, the cheaper Microsoft 365 Business Standard plan doesn’t include features such as Unified Audit Logging and Sensitivity Labels, both of which are useful for compliance.
- Increased Productivity: When users have the right tools for their roles, they can work more efficiently. Proper licence allocation ensures everyone has what they need – no more, no less. .
- Future-Proofing: Regular licence reviews help you stay ahead of technological changes, ensuring your business is always leveraging the most current and beneficial features. .
- Strategic IT Alignment: Licence management is a key part of aligning your IT capabilities with your broader business strategy, driving digital transformation and competitive advantage.
Proper licence management doesn’t need to be onerous, but it does require ongoing attention, expertise, and strategic planning. It’s about understanding your current needs, anticipating future requirements, and aligning your licensing strategy with your broader IT and business goals.
If you’re not actively managing your Microsoft 365 licences, you’re likely missing opportunities for cost savings, operational improvements, and enhanced security. More importantly, you may be compromising on tools that could drive your business forward in an increasingly digital world.
Getting Started with Licence Management
The first step towards improved licence management is to understand what licences you currently have in place. This is easily done from within Microsoft 365 Admin, or by asking your IT team to produce a report for you.
From there, you can review your current licence assignment against actual usage and business needs. This will help identify any discrepancies, such as overprovisioning or inactive licences still assigned to former employees.
At Grassroots IT, we believe that technology should be a strategic enabler for your business. Effective licence management is a key part of this strategy. It ensures you’re getting the most value from your Microsoft 365 investment, both in terms of cost-efficiency and operational capability.
Ready to stop overspending and start optimising your Microsoft 365 environment? Let’s have a conversation about how we can help you align your licences with your business needs and goals, ensuring you’re not just saving money, but setting your business up for future success.
In today’s business environment, many organisations are leveraging offshore teams to drive growth, reduce costs, and access a wider talent pool. However, this approach comes with its own set of challenges, particularly when it comes to cybersecurity. As businesses strive to protect their sensitive data and maintain compliance, they need robust solutions that can secure their offshore operations effectively. This is where Azure Virtual Desktop (AVD) comes in —a transformative technology that’s changing the way businesses tackle remote work security.
The Security Challenges of Offshore Teams
Before we dive into the solution, let’s consider some of the key security challenges that businesses face when working with offshore teams:
- Data Protection Across Borders: When your data travels across international boundaries, it becomes vulnerable to various threats and may be subject to different regulatory requirements.
- Device Management and Control: With team members using their own devices or locally provided hardware, ensuring consistent security standards becomes a significant challenge.
- Network Security Concerns: Relying on various local internet service providers and potentially unsecured networks can expose your business to numerous cyber threats.
- Compliance and Regulatory Issues: Different countries have different data protection laws, making it challenging to maintain compliance across a global workforce.
How Azure Virtual Desktop Addresses These Challenges
Azure Virtual Desktop offers a comprehensive solution to these security challenges, providing a secure, scalable, and manageable environment for offshore teams. Here’s how AVD tackles each of the challenges mentioned above:
- Centralised Data Storage and Processing: With AVD, all data and processing occur within the secure Azure cloud environment, not on local devices. This centralization significantly reduces the risk of data leakage and ensures that sensitive information never leaves your controlled environment.
- Robust Access Controls and Multi-Factor Authentication: AVD integrates seamlessly with Azure Active Directory, allowing you to implement strong authentication methods, including multi-factor authentication. This ensures that only authorised personnel can access your virtual desktops and applications.
- Simplified Device Management: Because processing occurs in the cloud, the specifications and security of local devices become less critical. This makes it easier to implement a Bring Your Own Device (BYOD) policy without compromising security.
- Network Security Features: AVD leverages Azure’s advanced networking features, including virtual networks, network security groups, and Azure Firewall. These tools help create a secure tunnel for data transmission, regardless of the local network infrastructure.
- Compliance Certifications and Capabilities: Microsoft Azure holds a wide array of compliance certifications, helping businesses meet various regulatory requirements. Additionally, features like Azure Information Protection can be used to classify and protect sensitive data, regardless of where it’s stored or who it’s shared with.
Azure Virtual Desktop vs. Alternative Solutions
While Azure Virtual Desktop offers a robust solution for securing offshore teams, it’s important to understand how it compares to alternative approaches. Let’s look at some common alternatives and how they stack up against AVD:
- Traditional VPN Solutions
- Pros: Familiar technology, can be less expensive initially
- Cons: Can be slower, especially for users in distant locations; may require significant infrastructure; can be complex to manage at scale
- Compared to AVD: AVD offers better performance, easier scalability, and more granular security controls
- Remote Desktop Services (RDS)
- Pros: Microsoft technology, familiar to many IT teams
- Cons: Requires Windows Server infrastructure & licensing; can be complex to set up for external access;
- Compared to AVD: AVD offers easier management, better scalability, and is designed for cloud-first deployments. AVD’s license is also included in various 365 plans such as M365BP.
- Local Workstations with Endpoint Management
- Pros: Users work on local hardware, which can be beneficial for some tasks
- Cons: Significantly higher security risks; challenges with data sovereignty; harder to ensure consistent user experiences
- Compared to AVD: AVD offers much stronger security controls and easier management, particularly for geographically dispersed teams
While each of these alternatives has its place, Azure Virtual Desktop stands out for its combination of security, performance, scalability, and integration with the Microsoft ecosystem. For businesses already leveraging Azure and Microsoft 365, AVD can be a natural extension of their existing infrastructure, offering a seamless and secure solution for managing offshore teams.
Key Benefits of Using AVD for Offshore Teams
Implementing Azure Virtual Desktop for your offshore teams offers several significant benefits:
- Improved Data Security: By keeping all data and processing in the Azure cloud, you significantly reduce the risk of data breaches and unauthorised access.
- Enhanced Productivity: AVD provides a consistent, high-performance experience for all users, regardless of their location or device, leading to improved productivity.
- Cost-Effectiveness: By leveraging cloud resources, you can avoid the need for expensive local hardware upgrades and reduce IT support costs.
- Scalability and Flexibility: Easily scale your virtual desktop infrastructure up or down based on your current needs, and quickly provision resources for new team members.
- Universal Accessibility: Access from any device, location, or operating system, including Mac, iPad, Android, and web browsers.
Real-World Example: Securing Offshore Operations with AVD
One of our clients, a growing financial services company, faced significant challenges in securing their offshore operations. They had team members spread across multiple countries, each with different cybersecurity landscapes and regulatory environments.
By implementing Azure Virtual Desktop, they were able to:
- Centralise all their data and applications in a secure Azure environment
- Implement strict access controls and multi-factor authentication for all users
- Provide a consistent, high-performance work environment for all team members, regardless of their location
- Ensure compliance with various international data protection regulations
- Significantly reduce the risk of data breaches and unauthorised access
The result? Our client now enjoys peace of mind knowing their offshore operations are secure, compliant, and efficient. They’ve been able to focus on growing their business without worrying about the security implications of their distributed workforce.
Conclusion
Azure Virtual Desktop offers a powerful solution for businesses looking to enhance the security of their offshore teams. By centralising data and processing in the secure Azure cloud, implementing robust access controls, and simplifying device management, AVD addresses many of the key security challenges associated with offshore work.
At Grassroots IT, we’ve helped numerous organisations implement and optimise Azure Virtual Desktop for their offshore teams. We understand the unique challenges businesses face in this area and have the expertise to help you leverage AVD to its full potential.
Ready to enhance the security of your offshore teams with Azure Virtual Desktop? Contact Grassroots IT today for a no-obligation consultation. Let’s work together to create a secure, efficient, and scalable environment for your global workforce.
Azure Virtual Desktop (AVD) is a cloud-based service that provides a complete virtual desktop infrastructure (VDI) solution. It allows users to access a Windows desktop environment and applications from anywhere, on any device, while leveraging the power and scalability of Microsoft Azure. AVD offers businesses the flexibility to create and manage virtual desktops and remote apps, making it easier to support remote work and bring-your-own-device (BYOD) policies.
In the world of remote work and cloud computing, Azure Virtual Desktop has emerged as a powerful solution for businesses seeking flexibility and scalability. While AVD offers significant benefits for a wide range of applications, there are scenarios where standard CPU-based instances may fall short. Enter GPU-enabled instances – a game-changer for organisations running graphics-intensive applications.
Understanding GPU-Enabled Instances in AVD
GPU-enabled instances in Azure Virtual Desktop leverage the power of graphics processing units to accelerate rendering and computational tasks. Unlike CPU-only instances, which rely solely on central processing units, GPU-enabled instances can offload graphics-intensive workloads to specialised hardware, resulting in significantly improved performance for certain applications.
Use Cases for GPU-Enabled AVD Instances
- Engineering and CAD Applications: GPU-enabled instances can significantly speed up computations and improve responsiveness in computer-aided design and engineering software. This is particularly beneficial for applications like AutoCAD when working on large, complex projects or performing resource-intensive tasks such as 3D solid modelling or photorealistic rendering.
- 3D Modelling and Design: Industries such as architecture, product design, and animation benefit greatly from GPU-enabled instances. These environments can handle complex 3D models and render high-quality visualisations much faster than traditional CPU-only setups. For example, AutoCAD, a widely used computer-aided design software, can leverage GPU acceleration for smoother 3D navigation and faster rendering of complex models.
- Data Visualisation and Analysis: Organisations dealing with large datasets and complex visualisations can leverage GPU power to generate insights more quickly and interact with data more smoothly. ArcGIS Pro, a professional GIS application for mapping and spatial analysis, is an excellent example of software that can benefit significantly from GPU-enabled instances, especially when working with large geographic datasets or performing complex spatial analyses.
Benefits of GPU-Enabled AVD Instances
GPU-Enabled AVD instances provide unique advantages over traditional CPU-based instances, including:
- Enhanced Performance: GPU acceleration can provide orders of magnitude improvement in performance for compatible applications.
- Improved User Experience: Smoother interactions and faster processing lead to higher productivity and user satisfaction.
- Flexibility for Remote Work: High-performance computing capabilities can be accessed from anywhere, enabling true flexibility for graphics professionals.
- Centralised Management and Security: IT teams can more easily manage and secure these high-powered workstations when they’re centralised in Azure.
Real-World Example: 3D Modelling with AVD
One of our clients, a mining engineering firm, faced challenges with their 3D modelling workflow. Their designers needed to collaborate on complex models, but their existing infrastructure couldn’t support remote work effectively. By implementing GPU-enabled Azure Virtual Desktop instances, we helped them achieve:
- Seamless remote access to high-performance workstations
- Improved collaboration as multiple team members could work on the same models simultaneously
- Enhanced security by keeping sensitive designs within the Azure environment
- Significant cost savings by eliminating the need for individual high-end workstations
The result? A more agile, productive team that could work from anywhere without compromising on performance or security.
Considerations When Choosing GPU-Enabled Instances
While GPU-enabled instances offer compelling benefits, they’re not always the best choice for every scenario. Here are some factors to consider:
- Cost Implications: GPU-enabled instances are generally more expensive than standard instances. It’s crucial to weigh the performance benefits against the additional costs.
- Workload Assessment: Analyse your specific workloads to determine if they truly require GPU acceleration. Some applications may not see significant benefits from GPU power.
- Scaling Considerations: Consider how your needs might change over time. GPU-enabled instances offer excellent scalability, allowing you to adjust resources as your requirements evolve.
- User Requirements: Not all users may need GPU-enabled instances. A hybrid approach, where only specific user groups are assigned GPU resources, can help optimise costs.
For many business applications, including standard office productivity tools, web browsing, and light data processing, CPU-only instances are often sufficient. It’s essential to perform a thorough analysis of your workloads and user needs before investing in GPU-enabled instances.
Getting Started with GPU-Enabled AVD
Implementing GPU-enabled Azure Virtual Desktop instances requires careful planning and expertise. At Grassroots IT, we’ve helped numerous organisations assess their needs, design optimal AVD environments, and manage the transition to GPU-enabled instances where appropriate.
Our approach involves:
- Comprehensive workload analysis
- Cost-benefit assessment
- Pilot testing with key user groups
- Full deployment and optimisation
- Ongoing management and support
At Grassroots IT, we’re committed to helping you navigate these decisions and implement solutions that truly drive your business forward. Whether you’re considering GPU-enabled AVD instances or exploring other cloud technologies, our team of experts is here to guide you every step of the way.
Ready to explore if GPU-enabled Azure Virtual Desktop instances are right for your business? Contact Grassroots IT today for a no-obligation consultation. Let’s work together to find the perfect solution for your unique needs.
You’ve likely heard buzzwords like “cloud services” and “mobile device management” floating around, and perhaps “Microsoft Intune” has come up in conversations with your IT provider or tech-savvy colleagues. But what exactly is Intune, and why should you care about it? Let’s break it down in plain English, so you can understand how this tool might benefit your business – without needing a degree in computer science.
The Basics: What is Microsoft Intune?
Microsoft Intune is a cloud-based service that helps businesses manage their devices and applications. Think of it as a central control panel for all the phones, tablets, and computers your team uses for work. It’s part of Microsoft’s broader suite of business tools, integrating seamlessly with other Microsoft 365 products, and is rapidly becoming a core part of how many businesses manage their IT systems.
What Does Intune Do?
Intune’s capabilities can be broken down into three main categories: Device Management, App Management, and Security.
Device Management
Intune gives you control over how company devices such as laptops are used. With Intune, you can set password requirements to ensure all devices have strong, secure passwords. You can control which apps can be installed, preventing potentially harmful or unproductive apps from being used on work devices. Intune also allows you to configure device settings, setting up email, Wi-Fi, VPN, and other settings automatically. Perhaps most crucially, if a device is lost or stolen, you can remotely wipe data from it, protecting your company’s sensitive information.
App Management
When it comes to apps, Intune is your central command centre. You can push necessary apps to all devices, ensuring everyone has the tools they need to do their job effectively. Intune also allows you to control which apps can access company data, keeping your sensitive information safe. It can update apps automatically, keeping everyone on the latest, most secure versions. And when an employee leaves the company, Intune makes it easy to remove business apps and data from their device, protecting your intellectual property.
Security
Security is paramount, and Intune has you covered. Microsoft Intune is a robust solution for managing and securing your organisation’s devices and data. It ensures that all devices are up to date with the latest security patches and updates, reducing vulnerabilities. Intune also integrates seamlessly with Microsoft Defender and other security products, creating a comprehensive security ecosystem. By enforcing policies such as data encryption and remote wipe, Intune protects sensitive information even if a device is lost or stolen. Additionally, it links with Entra ID to manage multi-factor authentication and conditional access policies, preventing unauthorised access to company resources. With Intune, you can confidently safeguard your business data against a wide range of security threats.
Why Should You Care?
Now that we understand what Intune does, let’s talk about why it matters for your business.
Intune offers flexibility, working with both company-owned devices and personal devices in a Bring Your Own Device (BYOD) environment. This means you can secure your data whether your team is using company laptops or their own smartphones.
Simplicity is another key benefit. Instead of your IT team dealing with each device individually, they can manage everything from one place. This can save significant time and reduce headaches.
Security is a major advantage of Intune. It allows you to protect your business data without making life difficult for your team. Intune’s security features work in the background, allowing your team to focus on their work rather than wrestling with cumbersome security protocols.
Productivity gets a boost with Intune. By ensuring your team has the right tools and access, wherever they’re working from, Intune provides seamless access to business resources while maintaining control.
Finally, Intune can be cost-effective. By managing devices and apps centrally, you can often reduce your overall IT costs and simplify budgeting.
Is Intune Right for Your Business?
Intune can be particularly useful in several scenarios. If you have a mobile workforce that works from various locations or uses multiple devices, Intune can help keep everyone connected and secure. If you’re concerned about data security (and in this day and age, who isn’t?), Intune provides robust security features to protect your business data.
If you’re tired of hearing about individual device issues and want to simplify your IT management, Intune can streamline your processes. If you’re already using other Microsoft 365 products, Intune integrates seamlessly, creating a cohesive ecosystem. And if you’re supporting a bring-your-own-device (BYOD) environment, Intune allows you to secure company data on personal devices without infringing on employee privacy.
Related: Securing Your Remote Workforce with Entra ID and Intune | Grassroots IT
Real-World Example
Let’s consider a scenario to see how Intune works in practice:
Imagine you run a small marketing agency with 20 employees. Half of your team works in the office, while the others work remotely or at client sites. Some use company laptops, others use their personal devices.
With Intune, you can ensure all devices (company-owned and personal) that access business data have the necessary security measures in place. Your team can easily access the apps and data they need, whether they’re in the office or at a client site. If someone’s device is lost or stolen, your IT team can quickly remove business data from that device. When you onboard a new employee, they can automatically set up the device with all necessary apps and settings. And if an employee leaves, they can remove business apps and data from their device without touching their personal information.
Wrapping Up
Microsoft Intune is a powerful tool that can help streamline your IT management, enhance your security, and boost your team’s productivity. While it may seem complex at first, the benefits it brings to your business can be significant.
Remember, good IT shouldn’t give you headaches – it should solve them. Intune is just one of the many tools that can help make your business technology work for you, not against you.
At Grassroots IT, we’ve been helping businesses like yours leverage tools like Intune for nearly two decades. We understand that every business is unique, and we’re here to help you navigate the world of modern IT solutions. Whether you’re ready to implement Intune or just want to learn more, we’d be happy to chat about how it could work for your specific needs.
Technology should be an enabler for your business, not a barrier. Let’s work together to make sure your IT is helping your business thrive.
The Power of Integrated Lifecycle Management
Managing the lifecycle of users and devices is a critical aspect of IT operations. From the moment a new employee joins your organisation to the day they leave, and from when a device is first enrolled to when it’s retired, there are numerous considerations involved in maintaining a secure, efficient, and productive IT environment.
Two powerful tools in the Microsoft 365 suite can help streamline this process: Entra ID (formerly Azure AD) and Intune. In this post, we’ll explore how these services work together to provide a comprehensive lifecycle management solution for your users and devices.
User Creation and Onboarding
The journey begins when a new user joins your organisation. Entra ID facilitates this process through a series of steps:
- Create the user account: Use the Azure portal to manually create the account, or leverage PowerShell scripts or HR system integration for automatic account creation
- Assign licenses and access rights: Grant the necessary licenses (such as Microsoft 365 Business Premium) and provide access to required resources. For organisations with defined roles, Entra ID’s group-based licensing can streamline this process.
- Enable multi-factor authentication (MFA): As a crucial security measure, add users to an MFA registration campaign to enforce MFA setup. Entra ID offers various options, including the Microsoft Authenticator app, SMS, or phone calls.
- Configure conditional access policies: Set up policies to control resource access based on specific conditions. For new users, you might require a password change on first login or restrict access to certain apps until they’ve completed necessary training.
- Provide necessary information to the user: Share login credentials, MFA setup instructions, and any other relevant information with the new user.
To streamline this process, consider creating a standardised onboarding workflow that automates as many of these steps as possible. This approach not only saves time but also ensures consistency in how new users are set up across your organisation.
Remember, user onboarding is more than just technical setup. It’s an opportunity to make a great first impression and set new team members up for success. Consider incorporating steps like sending a welcome email, scheduling an IT orientation session, or providing a digital welcome pack with key information about your organisation’s IT practices and policies.
Device Enrolment
Once a user account is set up, the next step is often to get them set up with a device such as a laptop. This is where Intune shines, offering a range of enrolment methods to suit different organisational needs and device types.
Company-Owned Devices
For company-owned devices, Intune allows you to pre-configure enrolment profiles. This proactive approach ensures that devices are compliant with your policies from the moment they’re turned on, saving time and reducing security risks.
BYOD Support
For organisations embracing Bring Your Own Device (BYOD) policies, Intune also supports personal device enrolment. In these scenarios, you can apply different policies that strike a balance between organisational security needs and user privacy.
Windows Autopilot
It’s worth mentioning Windows Autopilot as part of the same discussion as Intune and Entra ID. Windows Autopilot simplifies the device setup process, making new devices ready to use with minimal IT intervention. Here’s how it works:
- Devices are pre-registered with your organisation (often by the hardware vendor).
- When first turned on, the device automatically configures itself.
- It joins your Azure AD, enrols in Intune, and applies your predefined settings and policies.
Autopilot is particularly useful for remote workers, as devices can be shipped directly to them, ready to use out of the box. This approach saves time for IT teams and ensures consistency across all devices.
Ongoing Management
Once users are set up and devices are enrolled, the focus shifts to ongoing management. This is where the true power of Intune and Entra ID’s integration becomes apparent, offering a comprehensive suite of tools for maintaining security, compliance, and efficiency.
Security Policies
Intune allows you to create and apply security policies to your devices. These policies can cover a wide range of security measures, including:
- Device encryption requirements
- Restrictions on certain device features
By applying these policies, you can ensure that all devices, whether company-owned or personal, meet your organisation’s security standards.
App Management
With Intune, you gain granular control over app deployment and management. You can:
- Deploy both store apps and line-of-business apps to your devices
- Manage app updates to ensure all devices are running the latest, most secure versions
- Set up app protection policies to safeguard company data within applications
This level of control ensures that your users have access to the tools they need while maintaining security and compliance.
Compliance Monitoring
Intune continuously monitors devices for compliance with your policies. If a device falls out of compliance, you can configure automated actions, such as blocking access to company resources. This real-time monitoring and response capability helps maintain your security posture without constant manual oversight.
Access Management
As users’ roles change within your organisation, you can use Entra ID to adjust their access rights accordingly. This includes:
- Modifying group memberships to grant or revoke access to specific resources
- Updating license assignments as needed
- Managing privileged access through Entra ID’s Privileged Identity Management feature
This dynamic access management ensures that users always have the right level of access for their current role, no more and no less.
Through the integrated use of Intune and Entra ID, ongoing management becomes a dynamic, responsive process. It allows you to maintain security and compliance while providing users with the tools and access they need to be productive. This balance of security and usability is key to a successful modern workplace strategy.
Embracing Comprehensive Lifecycle Management
The integration of Entra ID and Intune provides a powerful solution for managing the entire lifecycle of users and devices in your organisation. From streamlined user onboarding to simplified device enrolment, and from robust ongoing management to comprehensive security and compliance features, these tools offer a holistic approach to modern IT management.
By implementing this integrated lifecycle management approach, organisations can:
- Enhance security posture through consistent policy application and advanced threat protection
- Improve efficiency by automating many routine IT tasks
- Ensure compliance with regulatory requirements through built-in features and detailed reporting
- Provide a better user experience with seamless access to necessary resources
- Adapt more quickly to changing business needs and evolving security threats
Particularly in a world where remote work is increasingly common, and security threats are ever-present, such a comprehensive approach to lifecycle management is no longer a luxury—it’s a necessity.
Whether you’re just starting your journey with Microsoft 365 or looking to optimise your existing setup, Grassroots IT is here to help. We can assess your current environment, design a tailored implementation strategy, and provide ongoing support to ensure your lifecycle management processes continue to meet your evolving needs.
The digital landscape has seen a fundamental shift in how businesses operate, with remote work becoming more than just a trend. While this flexibility brings numerous benefits, it also introduces new challenges in securing business data and maintaining a robust cybersecurity posture.
As your team members access sensitive information from various locations and devices, how can you ensure that your business data remains protected? Enter Microsoft Entra ID (formerly Azure AD) and Intune—two powerful tools that, when combined, provide a comprehensive solution for securing your remote workforce.
Understanding the Security Challenges of Remote Work
Before we dive into the solutions, let’s take a moment to understand the unique security challenges that come with remote work:
- Increased attack surface: With devices operating outside the corporate network, not only are traditional security controls such as corporate firewalls rendered powerless, but there are also more potential entry points for cybercriminals. This can include unsecured Wi-Fi networks, personal devices, and even the use of public computers.
- Data leakage risks: The use of personal devices for work purposes can lead to inadvertent data exposure. For example, a team member may unintentionally save sensitive company data on their personal cloud storage or accidentally share confidential information with unauthorised individuals.
- Policy enforcement difficulties: Maintaining consistent security policies across a distributed workforce can be challenging. Traditional methods of enforcing policy, such as Active Directory, are unreliable at best with a remote workforce. This can lead to inconsistent security practices and increased vulnerability.
- Shadow IT: Remote workers might resort to using unauthorised applications or services to get their work done, potentially exposing company data to unsecured platforms. This “shadow IT” can be difficult to detect and control in a remote environment.
Microsoft Entra ID: The Foundation of Identity Security
At the heart of securing your remote workforce is robust identity management. This is where Microsoft Entra ID shines.
Entra ID is a cloud-based identity and access management service that forms the backbone of security for Microsoft 365 and many other cloud applications. For securing and protecting remote workers, Entra ID offers several key benefits:
- Single Sign-On (SSO): Allows users to access multiple applications with one set of credentials, improving both security and user experience. This reduces the likelihood of employees using weak or repeated passwords across multiple services.
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring two or more verification methods to access resources. This significantly reduces the risk of unauthorised access, even if passwords are compromised.
- Conditional Access: Enables you to control access to your apps and data based on identity, device, and risk signals. For example, you can require additional authentication steps for access from unfamiliar locations or devices.
By implementing Entra ID, you create a strong foundation for securing your remote workforce’s identities and controlling access to your business resources. And the good news is, if you already have a Microsoft 365 subscription, you already have access to Entra ID.
Intune: Comprehensive Device Management for Remote Workers
While Entra ID secures identities, Microsoft Intune takes care of device and application management. Intune is a cloud-based service that focuses on mobile device management (MDM) and mobile application management (MAM).
Key features of Intune include:
- Device enrolment: Easily enrol and manage devices across various platforms (Windows, iOS, Android). This allows you to maintain control over both company-owned and personal devices used for work, even allowing you to remote-wipe a device in the event it becomes lost.
- Application management: Deploy and manage apps on remote devices, ensuring your team has the tools they need. This includes the ability to push required apps to devices and remove them when necessary.
- Device compliance: Set rules, assess device compliance and deploy policies to protect company data. For instance, you can require devices to have up-to-date antivirus software and encrypted storage.
With Intune, you can ensure that all devices accessing your business data—whether company-owned or personal—meet your security standards.
Combining Entra ID and Intune for Robust Security
The real magic happens when you combine the powers of Entra ID and Intune. Together, they provide a comprehensive security solution for your remote workforce:
- Conditional Access policies: Use Entra ID’s Conditional Access in conjunction with Intune’s device compliance to control resource access based on user, device, and risk factors. For example, you can require that devices be managed by Intune and compliant with your policies before allowing access to company resources.
- App protection policies: Protect your data at the application level, preventing unauthorised sharing or saving of company information. This is particularly useful for BYOD scenarios where you need to separate personal and work data on the same device.
- Automated enforcement: Ensure compliance requirements are met on remote devices without manual intervention. Non-compliant devices can be automatically blocked from accessing company resources until they meet the required standards.
Conclusion
Securing your remote workforce doesn’t have to be a headache. With Microsoft Entra ID and Intune, you have a powerful combination of tools at your disposal to protect your business data, manage devices, and ensure compliance—all while providing a seamless experience for your remote team.
By implementing these solutions, you’re not just reacting to the challenges of remote work; you’re proactively building a secure, flexible, and productive work environment for the future. You’re empowering your team to work from anywhere, without compromising on security.
Ready to take the next step in securing your remote workforce? At Grassroots IT, we’ve been helping businesses like yours navigate the complexities of IT security for almost 20 years. Get in touch today for a free consultation and let’s explore how we can empower your remote team while keeping your data safe.
Technology is an integral part of how non-profit organisations operate, communicate, and deliver their missions. However, the adoption of new technologies isn’t always smooth sailing. Many non-profits face a significant challenge: the digital divide among their stakeholders. This divide can exist between staff members, volunteers, and even beneficiaries, potentially hindering the organisation’s efficiency and impact.
But with the right strategies, your non-profit can bridge this digital divide and ensure that everyone in your organisation can benefit from technological advancements. Let’s dive into some practical approaches to make technology adoption more inclusive and effective.
Understanding the Digital Divide in Non-Profits
First, let’s get clear on what we mean by the “digital divide.” In the context of non-profits, it refers to the gap between those who have the skills and confidence to use digital technologies effectively and those who don’t. This divide can stem from various factors:
- Age differences (e.g., older staff members may be less comfortable with new tech)
- Educational background
- Access to resources (some team members might not have reliable internet at home)
- Prior exposure to technology
The impact of this divide can be significant. It can lead to communication breakdowns, inefficiencies in program delivery, and even frustration among team members. Ultimately, it can hinder your organisation’s ability to fully leverage technology to further its mission.
Surprisingly, one counter-intuitive observation from many years of working with non-profits is that the younger generation, although often extremely proficient with mobile apps, can sometimes struggle with using software on a computer. A clear demonstration of the impact of prior exposure to certain technologies and not others.
Assessing Your Organisation’s Digital Landscape
Before you can bridge the divide, you need to understand where it exists in your organisation. Here’s how to get started:

- Conduct a skills assessment: Create a survey to gauge the technology comfort levels of your staff and volunteers. Ask about their familiarity with different tools
- Hold focus groups: Bring together small groups to discuss technology use in more depth. This can reveal nuances that a survey might miss
- Observe and analyse: Watch how different team members interact with your current technologies. Are there particular tools or processes that seem to cause frustration?
Remember, the goal isn’t to judge or criticise, but to understand where support is needed most.
Developing a Training Strategy
Once you’ve identified the gaps, it’s time to fill them. A clear training strategy is key:
- Create tiered training programs: Not everyone starts at the same level. Offer beginner, intermediate, and advanced tracks for different skills
- Use diverse training methods: People learn differently. Offer a mix of
• In-person workshops for hands-on learners
• Video tutorials for visual learners
• Written guides for those who prefer to read at their own pace
• Peer-to-peer sessions where team members can learn from each other
- Implement ongoing support: Learning doesn’t stop after one training session. Set up a help desk, create an internal knowledge base, or designate “champions” who can provide ongoing assistance
Leveraging User-Friendly and Accessible Technologies
Choosing the right tools can make a big difference in adoption rates:
- Prioritise intuitive interfaces: Look for technologies with clean, straightforward designs. The less cluttered and complicated, the better
- Ensure accessibility: Choose tools that offer features like screen reader compatibility, keyboard navigation, and the ability to adjust text sizes. This isn’t just for those with disabilities – it can make the technology more usable for everyone
- Consider language needs: If your team is multilingual, look for tools that offer multiple language options
Fostering a Culture of Continuous Learning
Creating the right environment is crucial for successful technology adoption:
- Lead by example: Have leadership actively engage with new technologies and share their learning experiences
- Celebrate progress: Recognise and reward team members who make strides in adopting new tools or help others to do so
- Create safe spaces for learning: Host regular “tech playtime” sessions where staff can experiment with new tools without the pressure of immediate productivity
Addressing Infrastructure and Access Issues
Sometimes the divide isn’t just about skills, but access:
- Ensure adequate hardware: If possible, provide necessary devices to team members who need them. It may seem obvious, but no-one will easily learn a new system if their computer is old, slow and frustrating to use
- Consider BYOD policies: If team members prefer to use their own devices, create clear guidelines and support for this approach. Before allowing BYOD within your organisation be sure to consider the impact on cybersecurity, data privacy and ongoing tech support
- Plan for offline capabilities: For field workers or those in areas with limited connectivity, look for tools that can work offline and sync when a connection is available
Tailoring Adoption Strategies for Different Stakeholder Groups
One size doesn’t fit all when it comes to technology adoption:
- For older team members: Connect new technologies to familiar processes. For example, show how a new CRM system is like an advanced version of the contact lists they’ve always used
- For remote or field workers: Focus on mobile-friendly tools and provide extra support for troubleshooting on the go
- For volunteers: Create quick-start guides that get them up and running with essential functions quickly
Measuring and Monitoring Progress
Keep track of how your efforts are paying off:
- Set clear goals: Define what success looks like. Is it 100% of staff being able to use a specific tool? Improved efficiency in certain processes?
- Regularly reassess skills: Conduct follow-up surveys to see how comfort levels have changed
- Gather stories: Collect anecdotes about how improved technology skills have made a difference in day-to-day work
Conclusion
Bridging the digital divide in your non-profit is an ongoing process, but it’s one that can dramatically improve your organisation’s effectiveness and impact. By understanding your team’s needs, providing comprehensive support, choosing the right tools, and fostering a culture of learning, you can ensure that everyone in your organisation can benefit from the power of technology.
Remember, the goal isn’t to turn everyone into tech experts overnight. It’s about ensuring that technology enhances, rather than hinders, your team’s ability to carry out your mission. With patience, persistence, and the right strategies, you can create a more inclusive and technologically empowered non-profit.
When efficiency and impact are paramount, non-profit organisations are increasingly turning to advanced technologies to streamline their operations and amplify their reach. According to The Institute of Community Directors Australia “Our data shows that not-for-profits are moving quickly to embrace these new tools and the promise of increased productivity in a resource-constrained sector.”
Two game-changing technologies at the forefront of this transformation are Artificial Intelligence (AI) and Robotic Process Automation (RPA). These powerful tools have the potential to revolutionise how non-profits operate, allowing them to do more with less and focus more on their core missions.
Understanding AI and RPA
Before we dive into specific applications, let’s clarify what we mean by AI and RPA:
- Artificial Intelligence (AI) refers to computer systems that can perform tasks that typically require human intelligence. This includes learning from data, recognising patterns, and making decisions. Although AI has existed for many years it has only recently gained mainstream awareness when OpenAI launched ChatGPT to the public in 2022.
- Robotic Process Automation (RPA) involves using software “robots” to automate repetitive, rule-based tasks. These bots can interact with digital systems just like humans, but faster and with fewer errors.
While distinct, AI and RPA often work together extremely effectively. RPA handles routine tasks, while AI can be applied to more complex, decision-making processes.
AI Applications in Non-Profits
1. AI Chatbots for Instant Support
AI-powered chatbots can revolutionise how your non-profit interacts with stakeholders, providing immediate assistance around the clock:
- 24/7 Availability: Chatbots offer constant support for donors, volunteers, and beneficiaries, ensuring that help is always at hand
- FAQ Handling: By answering frequently asked questions, chatbots can significantly reduce staff workload, allowing team members to focus on more complex tasks.
- Guided Processes: Chatbots can walk users through donation processes or volunteer sign-ups, making these interactions smoother and more efficient.
- Instant Information: Provide quick access to information about programs and services, improving user experience and engagement
Implementing AI chatbots can lead to increased engagement, improved response times, and more efficient use of human resources. While custom-built chatbots are an option, in many cases you can also leverage existing AI platforms. For instance, Microsoft Copilot, integrated with Microsoft 365, can be used to create chatbots that interact with donors or volunteers through Teams or other Microsoft platforms.
2. Natural Language Processing for Grant Writing
Grant writing is a critical but often time-consuming task for non-profits. AI, specifically Natural Language Processing (NLP), can provide valuable assistance:
- Analysis of Successful Applications: NLP can analyse previously successful grant applications to identify common patterns, language, and structures that resonate with funders
- Content Suggestions: Based on the analysis, AI can suggest relevant statistics, case studies, or phrasings to include in new applications, potentially increasing their effectiveness
- Alignment Checking: AI can compare your proposal against a funder’s stated priorities and guidelines, ensuring better alignment and potentially increasing success rates.
- Writing Assistance: Some advanced NLP tools can even help with drafting sections of the proposal, which you can then refine and personalise (the old-fashioned way!).
By leveraging AI in grant writing, you can potentially increase your success rates and efficiency in securing crucial funding. Tools like Claude, an AI assistant developed by Anthropic, can be particularly useful in this context. Claude can help analyse past successful grants, suggest improvements to current drafts, and even assist in generating initial content for grant proposals.
3. Sentiment Analysis for Social Media
Understanding public perception is crucial. AI-powered sentiment analysis can provide valuable insights from social media:
- Monitoring Public Sentiment: AI can analyse social media posts to gauge public sentiment about your organisation or cause, helping you respond promptly to both positive and negative feedback.
- Identifying Trends: Sentiment analysis can spot emerging trends or issues in your field, allowing you to stay ahead of the curve and adjust your strategies accordingly.
- Campaign Impact Assessment: By analysing social media reactions, you can measure the impact of your awareness campaigns and adjust your approach in real-time
- Crisis Management: Early detection of negative sentiment spikes can alert you to potential crises, allowing for swift response and mitigation.
Sentiment analysis can help you stay tuned to your audience, adapt your messaging effectively, and manage online reputation proactively.
RPA Applications in Non-Profits
Robotic Process Automation (RPA) offers significant potential for non-profits to streamline operations, reduce errors, and free up staff time for more strategic work. Here’s a deeper look at how you can apply RPA in your organisation:
1. Automating Data Entry and Processing
RPA can significantly reduce the time spent on manual data entry tasks, improving accuracy and efficiency:
- Inputting donation information: Create bots to extract donation details from various sources (e.g., email, web forms, spreadsheets) and automatically input them into your central database. This not only saves time but also reduces the risk of data entry errors
- Processing volunteer applications: Develop RPA workflows to screen volunteer applications, check for completeness, and even perform initial eligibility checks based on predefined criteria. This can speed up your volunteer onboarding process
- Updating contact information: Implement bots that can scan incoming emails or forms for updated contact details and automatically update your CRM or database systems. This ensures your contact lists remain current with minimal manual intervention
2. Streamlining Financial Processes
Financial tasks that follow set rules are prime candidates for RPA, allowing for faster processing and improved accuracy:- Reconciling bank statements: Develop bots to match transactions in your accounting software with bank statements, flagging discrepancies for human review. This can significantly reduce the time spent on monthly reconciliations
- Processing expense reports: Implement RPA to validate expense reports against company policies, check for required documentation, and even initiate reimbursement processes for approved expenses
- Invoice processing: Automate the capturing of invoice data, matching with purchase orders, and routing for approval, significantly speeding up your accounts payable process
3. Simplifying Reporting and Compliance Tasks
RPA can assist with the often-time-consuming task of creating reports, ensuring accuracy and timeliness:
- Automatically gathering data for annual reports: Create bots that can extract relevant data from various internal systems (financial, program management, CRM) to compile information needed for annual reports. This not only saves time but also reduces the risk of data inconsistencies
- Generating compliance documents for regulatory bodies: Develop automated processes to gather required data, populate standardised forms, and generate compliance reports for various regulatory bodies. This helps ensure timely submission and reduces the risk of non-compliance
- Grant reporting: Automate the collection and compilation of data required for grant reporting, ensuring you meet reporting deadlines and maintain positive relationships with funders
Getting Started with AI and RPA
If you’re considering implementing AI or RPA in your non-profit, here are some steps to get started:
- Identify Pain Points: Look for repetitive, time-consuming tasks that could be automated, or areas where better predictive capabilities could improve decision-making
- Assess Data Quality: Both AI and RPA rely on good data. Ensure your data is accurate, consistent, and well-organised
- Start Small: Begin with a pilot project in one area of your operations. This allows you to learn and adjust before scaling up. For instance, you might start by using Microsoft Copilot to assist with drafting donor communications or Claude to help with initial grant proposal drafts
Conclusion
AI and RPA offer exciting possibilities for non-profits to increase their efficiency and impact. By automating routine tasks and leveraging data for better decision-making, these technologies allow organisations to focus more on their core missions and less on administrative burdens.
However, it’s important to approach these technologies thoughtfully. They are tools to augment and support your team, not replace them. The goal is to free up your staff to focus on the high-value, human-centric work that is at the heart of what non-profits do.
If you’re interested in exploring how AI and RPA could benefit your organisation, we’d be happy to discuss your specific needs and help you chart a path forward. Together, we can harness the power of technology to create meaningful change in the world.
Limited resources, diverse stakeholder needs, and the pressure to demonstrate impact – all contribute to the complexity of non-profit operations and emphasise the critical need for efficient workflows. Fortunately, Microsoft 365 offers a suite of powerful tools that can help streamline processes, enhance collaboration, and boost productivity. Let’s explore five key Microsoft 365 tools that can transform how your non-profit works.
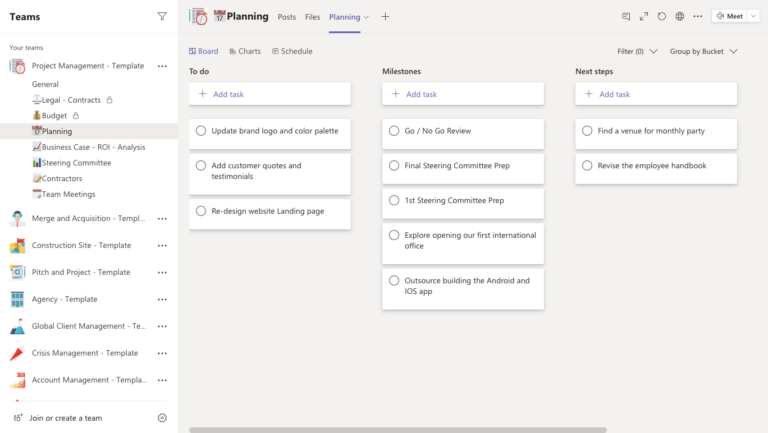
1. Microsoft Planner: Streamline Task Management
Microsoft Planner is a user-friendly task management tool that can significantly improve your team’s productivity. In fact, here at Grassroots IT we use Planner on a daily basis to keep team meetings organised and track actions & accountabilities.
Here’s how it can benefit your non-profit:
- Visual Task Boards: Create Kanban-style boards to visualize your projects and track progress at a glance.
- Security Considerations: Running an unsupported operating system can expose your business to increased security risks, as Microsoft will no longer release security fixes and updates for issues that are discovered. Cybercriminals often target systems that no longer receive regular security updates.
- Integration: Planner integrates seamlessly with other Microsoft 365 tools, making it easy to attach documents from SharePoint or OneDrive, or discuss tasks in Teams.
By using Planner, your non-profit can ensure that all team members are aligned on project goals, deadlines, and responsibilities, leading to more efficient project execution.
2. SharePoint: Centralise Document Management
SharePoint is a powerful platform for document management and collaboration. Not only that, but in preparation for AI tools such as Microsoft Copilot, SharePoint is the person place to store company information. For non-profits, it offers several key advantages:
- Centralised Document Storage: Create a single source of truth for all your organisation’s documents, accessible from anywhere
- Version Control: Track changes and maintain a history of document revisions, crucial for maintaining accuracy in reports and proposals
- Intranet Capabilities: Build internal websites to share news, updates, and resources across your organisation
- Granular Permissions: Control who can access, edit, or share specific documents or sites, ensuring data security
With SharePoint, your non-profit can improve information flow, reduce time spent searching for documents, and enhance collaboration across departments.
3. Microsoft Teams: Enhance Communication and Collaboration
Microsoft Teams is a hub for teamwork, bringing together chat, video meetings, file storage, and application integration. At Grassroots IT with a diverse team spread across five countries, we rely heavily on Teams to keep our people connected.
For non-profits, Teams can:
- Facilitate Remote Work: Host virtual meetings, share screens, and collaborate in real-time, regardless of team members’ locations
- Organise Conversations: Create channels for different projects or departments, keeping discussions focused and easily searchable
- Integrate Apps: Bring other Microsoft 365 tools and third-party apps into your Teams workspace for a seamless experience?
- External Collaboration: Invite volunteers, donors, or partners to specific teams or channels, fostering better stakeholder engagement
By leveraging Teams, your non-profit can break down communication silos and create a more connected, collaborative work environment.
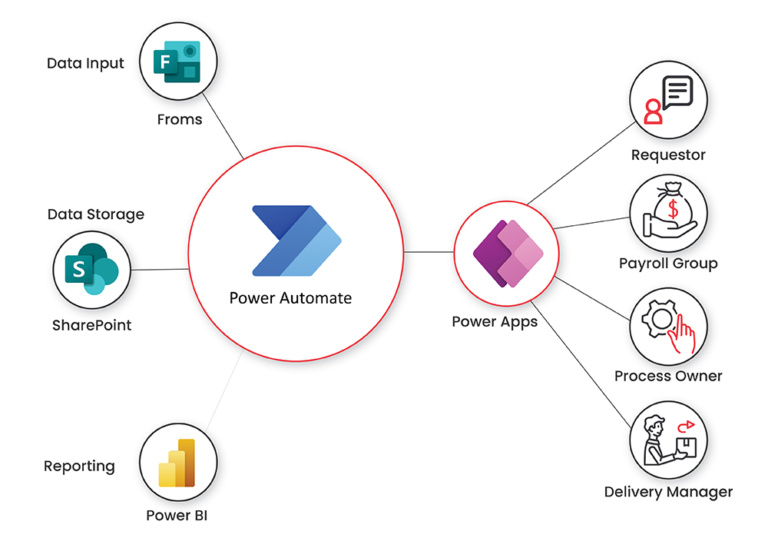
4. Power Automate: Streamline Repetitive Tasks
Power Automate (formerly known as Flow) is a powerful tool for creating automated workflows. Here’s how it can benefit your non-profit:
- Time-Saving Automation: Automate repetitive tasks like data entry, email notifications, or approval processes.
- Cross-Application Workflows: Create flows that work across different Microsoft 365 apps and even third-party services.
- Triggered Actions: Set up automated actions based on specific triggers, such as sending a thank-you email when a new form submission is received
- Templates: Use pre-built templates to quickly implement common automation scenarios.
By automating routine tasks with Power Automate, your non-profit can free up valuable time for more strategic, mission-focused work.
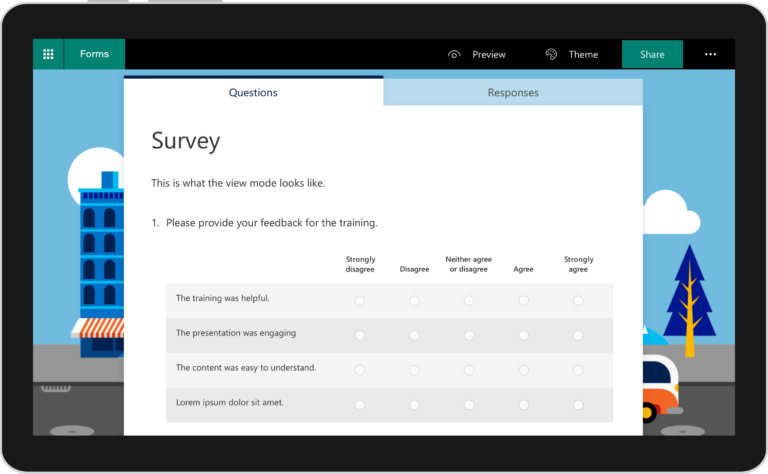
5. Microsoft Forms: Streamline Data Collection and Surveys
Microsoft Forms is a simple yet powerful tool for creating surveys, quizzes, and polls. For non-profits, it offers several benefits:
- Easy-to-Create Surveys: Build professional-looking forms and surveys without any technical expertise
- Real-Time Analytics: Get instant insights with automatic charts that update as responses come in
- Integration with Other Tools: Easily export data to Excel for deeper analysis or use Power Automate to trigger actions based on form responses
- Accessible and Responsive: Forms work on any device, making it easy to collect data from volunteers, donors, or beneficiaries in the field
- Multilingual Support: Create forms in multiple languages to reach diverse audiences
Microsoft Forms can help your non-profit gather valuable feedback, conduct needs assessments, or even manage event registrations with ease.
Final Thoughts
These five Microsoft 365 tools – Planner, SharePoint, Teams, Power Automate, and Forms – offer a powerful ecosystem to revolutionize your non-profit’s workflow. By leveraging these tools, you can enhance collaboration, streamline processes, and ultimately increase your organisation’s impact.
Remember, the key to success with these tools lies in thoughtful implementation and user adoption. Consider starting with one or two tools that address your most pressing needs, and gradually expand your use as your team becomes more comfortable with the new systems.
At Grassroots IT, we’re here to help you navigate the world of Microsoft 365 and find the best solutions for your non-profit’s unique needs. Reach out to us to learn more about how we can support your journey to a more efficient, tech-enabled workflow.
With Windows 10 going end-of-life in October 2025, many businesses are already considering their next steps. While your current setup might be working just fine, it’s important to start planning for the future. Let’s explore what the transition to Windows 11 means for your organisation and how to approach it sensibly.
Why Consider Windows 11 Now?
You might be wondering, “If it ain’t broke, why fix it?” It’s a fair question. However, there are a few key reasons to start thinking about retiring older computers in favour of Windows 11.
- Windows 10 End of Support: Microsoft has announced that Windows 10 will reach its end of support on October 14, 2025. After this date, there will be no more security updates or technical support for Windows 10. In addition, many Technology Service Providers (including Grassroots IT) explicitly exclude end-of-life operating systems from support agreements, meaning that any problems that do occur will incur additional fees to resolve.
- Security Considerations: Running an unsupported operating system can expose your business to increased security risks, as Microsoft will no longer release security fixes and updates for issues that are discovered. Cybercriminals often target systems that no longer receive regular security updates.
- Gradual Transition: Starting the transition process early allows for a more measured, less disruptive approach. It gives your team time to adapt gradually rather than rushing at the last minute, and eases strain on cashflow.
What’s New in Windows 11?
While not revolutionary, Windows 11 does offer some improvements. These include a cleaner, more modern interface, improved multitasking capabilities, and new features such as the ability to run Android apps. However, it’s important to acknowledge that these changes may not be significant enough to justify an immediate upgrade for all businesses.
- Enhanced security features
- A more intuitive user interface
- Better support for hybrid work environments
- Improved performance, especially for newer hardware
Planning your Transition
Assess your current setup
Before making any moves, it’s crucial to understand your current IT environment to ensure that there won’t be any nasty surprises along the way, such as important software applications that aren’t compatible with Windows 11. Consider the following:
- Which devices are compatible with Windows 11?
- Are there any critical applications that might have compatibility issues?
- What’s your current Windows 10 version, and how far are you from Windows 11 requirements?
Develop a timeline
With the end-of-support date of October 2025 in mind, create a realistic timeline for your transition. For many organisations the transition to Windows 11 will entail retiring older computers and replacing them with new computers running Windows 11, rather than installing the newer operating system on older, slower hardware.
When developing a timeline consider:
- Budgeting cycles for potential hardware upgrades
- Least disruptive times for your business operations
- Time needed for testing and addressing any compatibility issues
Prepare your team
Change can be challenging, but good communication can ease the process. Educate your team about the benefits of Windows 11 and involve them in the planning process. Address any concerns they may have and provide training on new features and changes to the interface.
- Inform your team about the upcoming changes and why they’re necessary
- Provide resources for self-learning about new features
- Consider offering training sessions closer to the transition date
How to Approach the Transition
- Start with a pilot: Begin by upgrading a small group of users who can provide feedback and help identify any issues. Many organisations will already have at least a handful of Windows 11 computers in place, effectively providing a pilot for the rest of the organisation.
- Address compatibility: Work with your IT team or partner to resolve any software or hardware compatibility challenges. Having people from different departments pilot Windows 11 is a good way to ensure you identify any potential issues well in advance of a full deployment.
- Roll out in phases: Gradually transition different departments or teams to minimize disruption to your operations. For many organisations choosing to progressively replace older computers, this will often span across teams & departments, helping to mitigating any focused disruption.
- Provide support: Ensure your team has access to resources and support during and after the transition. This may take the form of cheat-sheets, self-paced learning or even on-site technical support on the day of transition.
Final Thoughts
While there’s no need to rush into Windows 11 at this stage, it’s wise to start planning your transition strategy now. By taking a proactive approach, you can ensure a smooth upgrade process and avoid the security risks of running an unsupported operating system.
Remember, every organisation’s needs are unique. If you’re unsure about how to approach this transition or have concerns about compatibility with your current systems, don’t hesitate to reach out to Grassroots IT for assistance. We can provide tailored advice and support to ensure your transition is as smooth and beneficial as possible.
Stay proactive, stay secure, and let’s navigate this transition together.