What is phishing?
Phishing is a form of cyberattack whereby fake emails are sent to your staff with the intention of tricking them into sharing password details, granting access to a secure system, or otherwise taking some action to benefit the cybercriminal. Of the various types of cyberthreat that your organisation is likely to experience, phishing will be the most common, making it vital that you can quickly identify a phishing email.
Ideally you will have security systems in place, such as good email filtering, to ensure that phishing emails are blocked before even reaching your inbox. Unfortunately, even with good security systems in place, it’s not uncommon for the occasional phishing email to slip through.
With the average cost of a data breach in Australian now at $4.4 million, and over 82% of all data breaches involving some form of ‘human element’ (such as accidentally engaging with a phishing email), you can see why it’s important to be able to identify a phishing email, and to know how to respond safely.
What are the different types of phishing?
Over the last few years several distinct types of phishing attack have emerged. They all have the same ultimate intent but take slightly different approaches to achieving it.
Phishing
The most common form of phishing attack involves the cybercriminals casting a wide net, with fake emails sent indiscriminately and often in huge numbers. These emails are generally not targeted to their recipients in any meaningful way, apart from pretending to be from well-known brands that the recipient is likely to have some level of trust in, such as Commonwealth Bank or Microsoft. Phishing emails seek to trick the recipient into either sharing personal data or installing malicious software onto their computer to enable further attack.
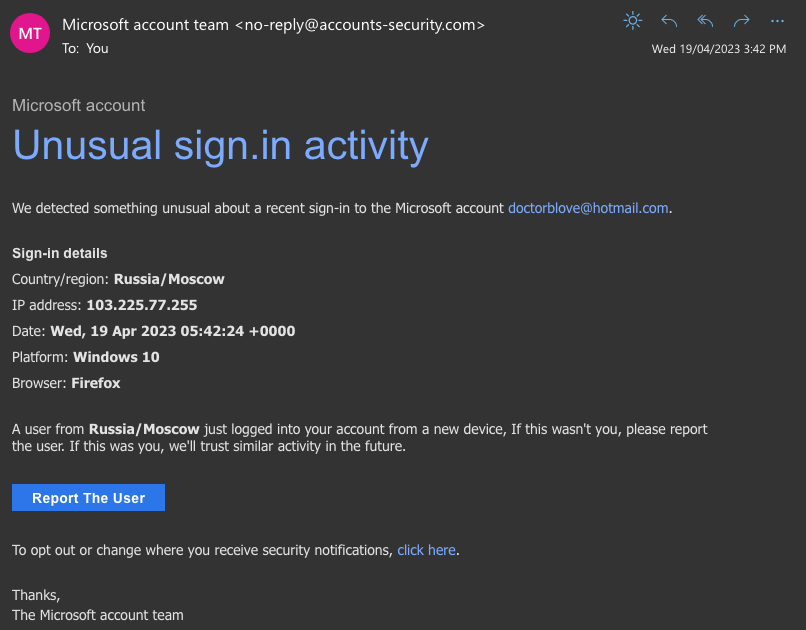
Spear Phishing
Spear phishing is similar to standard phishing, with the one difference being that spear phishing is targeted at and personalised for specific individuals. This requires the attackers to have some personally identifiable information on their victims, such as email address, first and last names and job title.
This slightly more sophisticated form of attack takes more time to craft and will therefore generally target victims with a higher perceived value, such as more senior staff or those likely to have access to higher value systems.
Whaling
Whaling is a further evolution of spear phishing, targeting senior executives and others in privileged positions. Whaling emails are individually crafted based on specific knowledge of the target organisation and key individuals, and often play on the pretext of a busy executive asking for some information or action to be taken urgently (such as the transfer of funds to a specific bank account).
Smishing
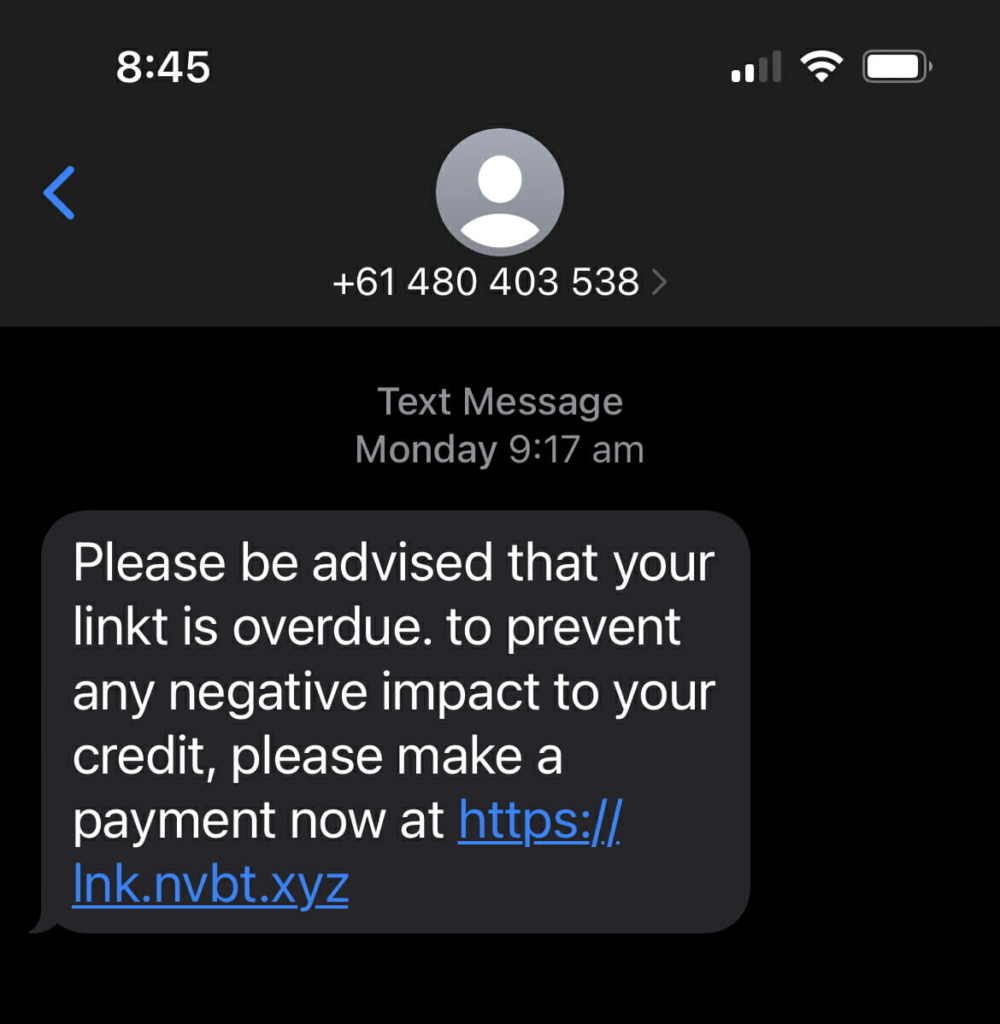
Smishing is a variant of phishing that uses SMS messages rather than emails to trick the recipient into clicking on a fake link and sharing personal data. Common examples in Australia may pretend to be from familiar brands such as Australia Post and Linkt.
Why is email phishing so common?
Of all the different types of cyberattack, why is phishing so prevalent? First is the fact that phishing attacks can be extremely cheap and easy to execute. Email use is extremely commonplace, providing a vast audience of potential targets, while the tools required to execute an attack can be obtained cheaply and easily on the dark web.
The second key point is that humans are – well – human. We can be extremely susceptible to influence through common psychological techniques, such as our tendency to follow rules. We also tend to make mistakes, many of which pass without consequence, but some (such as clicking on the wrong email link) may not.
We can also add that at an organisational level there is often a lack of cybersecurity awareness, meaning staff simply do not recognise a phishing email, nor do they know how to safely respond when they do
Read more: Building a culture of cybersecurity awareness in your business
How to identify a phishing email
To protect against a phishing attack, it’s extremely important that you be able to identify a phishing email so that you can delete it safely, and not accidentally fall prey. The good news is that there are some common identifiers that you can look out for. After just a little bit of practice you will quickly recognise a malicious phishing email without a second thought.
Unfamiliar sender
Phishing emails will often purport to come from either a generic corporate sender, or a person that you are unfamiliar with. This isn’t to say that you won’t ever receive legitimate email from an unfamiliar sender, but when you do, be cautious to validate it carefully.
Generic greetings
Given that most attackers will not have any personal information about you beyond your email address, phishing emails are likely to use generic greetings such as “Dear Sir”, rather than identifying you by name.
Urgent call to action
Phishing emails often convey a sense of urgency, encouraging you to ‘click now’ to claim a reward or avoid a penalty.
Too good to be true
Phishing emails may contain an offer that’s too good to be true. How likely is it that your long lost (and forgotten) great-aunt has died and left you a million dollars?
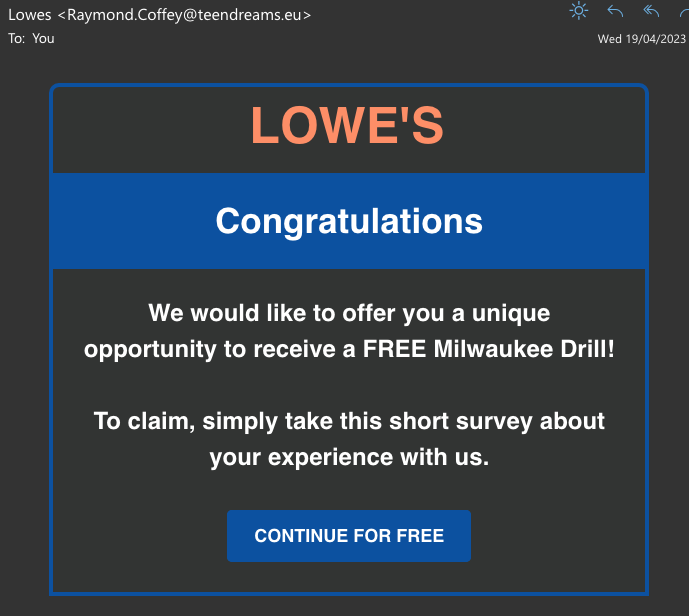
Bad spelling & grammar
Phishing emails often contain bad spelling and grammar, something you’re unlikely to see from a legitimate, professional organisation. This poor use of language may be due to an amateur translation from a foreign language, or it may be intentional in an attempt to avoid email filters.
Request for sensitive information
Many phishing attacks will try to get personal information from you, such as passwords or credit card details. Legitimate organisations will never ask for such information via email.
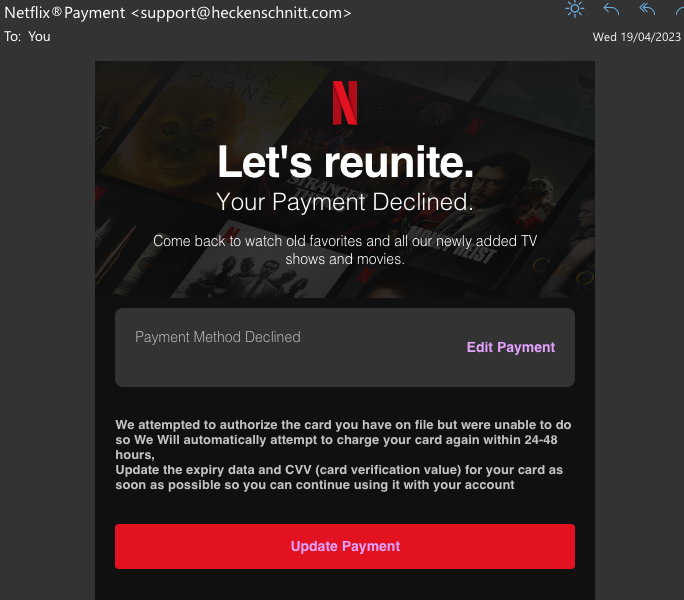
Inconsistencies in email addresses, links & domain names
All legitimate organisations have their own domain name, such as “grassrootsit.com.au” which they will use for their website and their email addresses. Capitalisation of domain names isn’t important; however, all other spelling and punctuation is. Phishing email will often come from email addresses that clearly don’t use the purported organisation’s domain name, or in some more sophisticated phishing attacks may use a domain name that closely matches the legitimate one, but with a sneaky minor change.
Suspicious links
As with email addresses, any links offered in a legitimate email should use the sending organisation’s proper domain name. Check all links carefully before clicking them to ensure that they do in fact use the correct and legitimate domain name. You can check the link address by hovering your mouse curser over the link without clicking.
Unexpected attachments
Always be suspicious of attachments on emails that you weren’t expecting, especially when the email is from an unfamiliar sender. Email attachments are an effective way for attackers to infect your computer with malicious software, but that can only happen if you open the attachment.
What to do if you receive a phishing email
Once you’re familiar with the common tell-tale signs of a phishing email, it will be clear as day when you next receive one. What you do next is crucially important.
The most important thing to remember is to not click on any links or attachments in the email, and to immediately delete the email. Some organisations may ask staff to report any phishing emails to their IT department, in which case you should follow the process provided and do so.
If you do accidentally click on either a link or an attachment in a phishing email, notify your IT department immediately and follow their instructions. There is a good chance that no harm has been done, but it is better to be safe than sorry.
Phishing is the most common form of cyberattack that you are likely to experience, but with a little knowledge it’s easy to identify a phishing email and take appropriate steps to avoid a security incident.